
On Friday, the Python Package Index (PyPI), the official repository of third-party open-source Python projects announced plans to mandate two-factor authentication requirement for maintainers of "critical" projects.
Although many community members praised the move, the developer of a popular Python project decided to delete his code from PyPI and republish it to invalidate the "critical" status assigned to his project.
PyPI rolls out 2FA for top 1% projects
Yesterday, admins of the PyPI registry announced they were in the process of introducing two-factor authentication (2FA) requirement for projects deemed "critical."
Any PyPI project accounting for the top 1% of downloads over the last six months as well as PyPI's dependencies have been designated critical.
"In order to improve the general security of the Python ecosystem, PyPI has begun implementing a two-factor authentication (2FA) requirement for critical projects. This requirement will go into effect in the coming months," announced the admins in a blog post.
Additionally, the maintainers of critical projects are being offered free hardware security keys, with support from the Google Open Source Security Team, a sponsor of Python Software Foundation (PSF).
We’ve begun rolling out a 2FA requirement: soon, maintainers of critical projects must have 2FA enabled to publish, update, or modify them.
— Python Package Index (@pypi) July 8, 2022
To ensure that these maintainers can use strong 2FA methods, we're also distributing 4000 hardware security keys!https://t.co/gcCNWSqBcU
The initiative follows recent repeated incidents of legitimate software libraries getting hijacked—across both the npm and PyPI ecosystems.
Last year, heavily used npm libraries, 'ua-parser-js,' 'coa' and 'rc' were altered with malware after a compromise of their maintainer accounts. As such, npm's parent company, GitHub, took steps to roll out an enhanced login experience (2FA options) for developers starting December 2021, with further security updates announced this May.
With the most recent news of PyPI project 'ctx' getting hijacked, as BleepingComputer first reported, and the case later turning out to be an "ethical" hacking experiment gone wrong, PyPI has followed GitHub's lead in also implementing 2FA for maintainer accounts.
"Ensuring that the most widely used projects have these protections against account takeover is one step towards our wider efforts to improve the general security of the Python ecosystem for all PyPI users," explains PyPI admins who have also shared a dashboard showing over 3,818 PyPI projects and 8,218 PyPI user accounts that they have identified as "critical" and who will likely be asked to adopt 2FA.
In spite of this, over 28,000 PyPI user accounts (including those not associated with a "critical" project) have voluntarily enabled 2FA.
Developer pushes back at mandatory 2FA
Although most [1, 2, 3] have reacted favorably to the move and welcomed PyPI's initiative towards enhancing the overall security of the software supply chain, some have not.
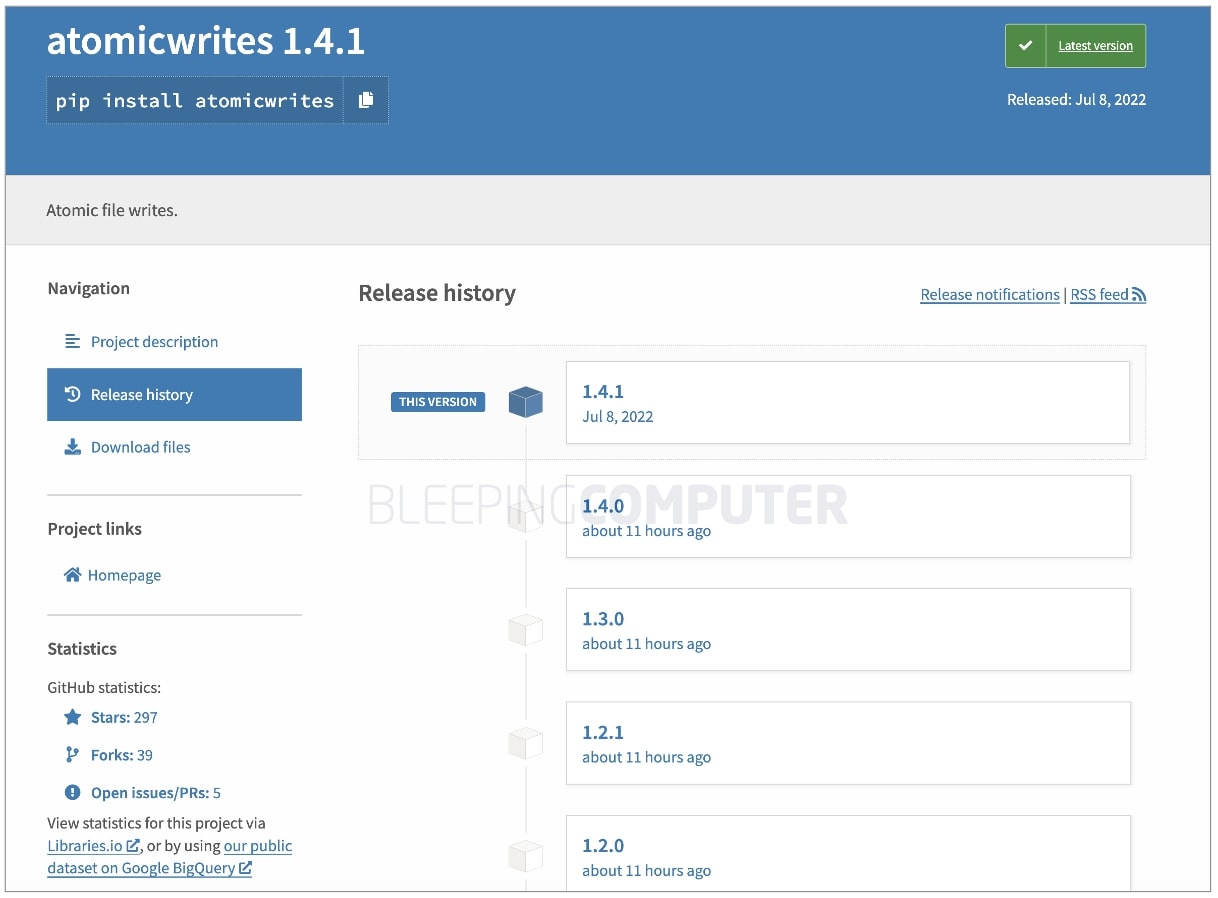
Markus Unterwaditzer, developer of the 'atomicwrites' PyPI project decided to delete his code from the registry after receiving a "Congratulations!" email from PyPI notifying the developer of his project having been deemed critical and now requiring two-factor authentication.
Note, Unterwaditzer's atomicwrites reportedly gets downloaded over 6 million times in a given month.
nice, I just deleted the atomicwrites package, then uploaded a new version. now it's no longer a critical project
— Markus Unterwaditzer (@untitaker) July 8, 2022
Some compared this move to 2016's left-pad incident that involved another developer almost breaking the internet by withdrawing his critical JavaScript projects from the npm registry.
Looks like Python just had a left-pad like incident.@pypi today required 2FA for top 1% downloaded projects.
— Paulus Schoutsen (@balloob) July 8, 2022
Author of python-atomicwrites hates it. Deletes their package, re-creates it and uploaded a new version and is no longer marked as critical. Now all old versions gone!
Although, in this case, Unterwaditzer simply re-published versions of 'atomicwrites' to reset his project's download counts (and hence its "critical" project status assigned by PyPI) as opposed to permanently withdrawing his code. By contrast, the circumstances surrounding the 'left-pad' incident were somewhat different and involved a trademark dispute.
"I decided to deprecate this package. While I do regret to have deleted the package and did end up enabling 2FA, I think PyPI's sudden change in rules and bizarre behavior wrt package deletion doesn't make it worth my time to maintain Python software of this popularity for free. I'd rather just write code for fun and only worry about supply chain security when I'm actually paid to do so," wrote Unterwaditzer.
BleepingComputer observed Unterwaditzer has indeed republished all versions of his project shortly after removing them within the last 24 hours:
Other community members chimed in on the matter as well:
Hot take: the real problem is not all those @pypi maintainers not using 2FA, it's the number of critical projects with one only overly-worked maintainer who is just a few months away from abandoning their project
— Chris Holdgraf (@choldgraf) July 9, 2022
Armin Ronacher, the creator of Python-based micro web framework. Flask argued:
"...when I create an Open Source project, I do not chose to create a 'critical' package. It becomes that by adoption over time," wrote Ronacher.
"Right now the consequence of being a critical package is quite mild: you only need to enable 2FA. But a line has been drawn now and I'm not sure why it wouldn't be in [PyPI's] best interest to put further restrictions in place."
"Instead of putting the burden to the user of packages, we're now piling stuff onto the developer who already puts their own labor and time into it. From the Index' point of view there is a benefit to not enforce rules on everybody as some of these rules might make the use of the index burdensome, but putting the burden only on critical packages does not hurt the adoption just as much," further writes the developer.
The repeated malware incidents and attacks involving open source software components have forced registry administrators to step up security across their platforms. It remains yet to be seen how well would the added burden of securing their projects, in addition to developing them, aligns with the expectations of an open source software developer.
The Board Report Deck CISOs Actually Use
CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.









Comments
SeZell - 3 years ago
Wow, if using a common sense security practice like 2FA is an issue, hopefully their code has been well reviewed for security vulnerabilities.
Everyone should be leery of a repository that DOESN'T require 2FA for developers.
yawnshard - 3 years ago
I cannot agree more. Such disrespect for the security of other people depending on your work just shows how it really is just a chore to them and they don't like the users (anymore).
Abandoning it and letting someone more competent and less burned-out fork it is preferable.
h_b_s - 3 years ago
Wow. Seriously? Guy's complaining because he needs to enhance the security of his PyPI account? This isn't about his code being "critical", that's just an excuse. Someone shouldn't have to be paid to care about security. Anyone that acts like this over sensible account security shouldn't be trusted for anything at all.
People, if you use his Python package, you might want to import the source, move it to an internal repository and reject anything this guy does in the future.
No one should have to be paid to worry about security. This isn't 1970. It's 2022 and security is EVERY EFFIN ONE'S RESPONSIBILITY because anyone is a target even if it's just for shits and giggles.
jimmyjones1256 - 3 years ago
All of this and they ended up doing it anyway. Leaving the aftermath of their mess affecting others (assuming the older versions haven't been reinstated).
xafase - 3 years ago
Until MFA is as cheap, frictionless, as fast as password, and everyone decides to use and set it up the same way, MFA is a pain in the ass that offer more problems than solutions.
ConjurerOfWorlds - 3 years ago
Anyone wanna tell them that all of those requirements have been easily implemented for years now? For example, if you want to log into the PyPI repository, plug this key into your USB first....aaaand, you're done.
Enterprise solutions like Microsoft's and Ping.ID's are just as easy. Username, password, now click the button that just popped up on your phone.
xafase - 3 years ago
USB dongles are not free. Cost quite a bit. Are a pain to use. And one type will not work on all my devices.
My phone, which one of the primary uses of is porn in the shower, is not a security device and should not be treated as such.
SeZell - 3 years ago
Except in this case, they are free. They sent developers one for free.
Phones make the most sense, because everyone already has one, and it's easy to do.
xafase - 3 years ago
Doesn't negate the fact that my phone is not a secure device and I refuse to let Google and Microsoft tell me how I am suppose to use MY computing devices.
Wow 4000. Only 6,999,996,000 to go!
ConjurerOfWorlds - 3 years ago
Ok, well, so long as we're clear that it's you making it more difficult on yourself than it needs to be, and not an inherent flaw in MFA.
TsVk! - 3 years ago
Markus Unterwaditzer seems like a bit of a ass. It really can't be that much drama to press a button on his free authentication dongle... noooo.
Some people just can't help themselves.
OrangeCode - 3 years ago
Crazy behaviour. Curious to see what impact this has on the open source community in general - weed out the ones that truly do not care about security. Its an eco system that our industry relies on and we must adopt more secure development practices.