
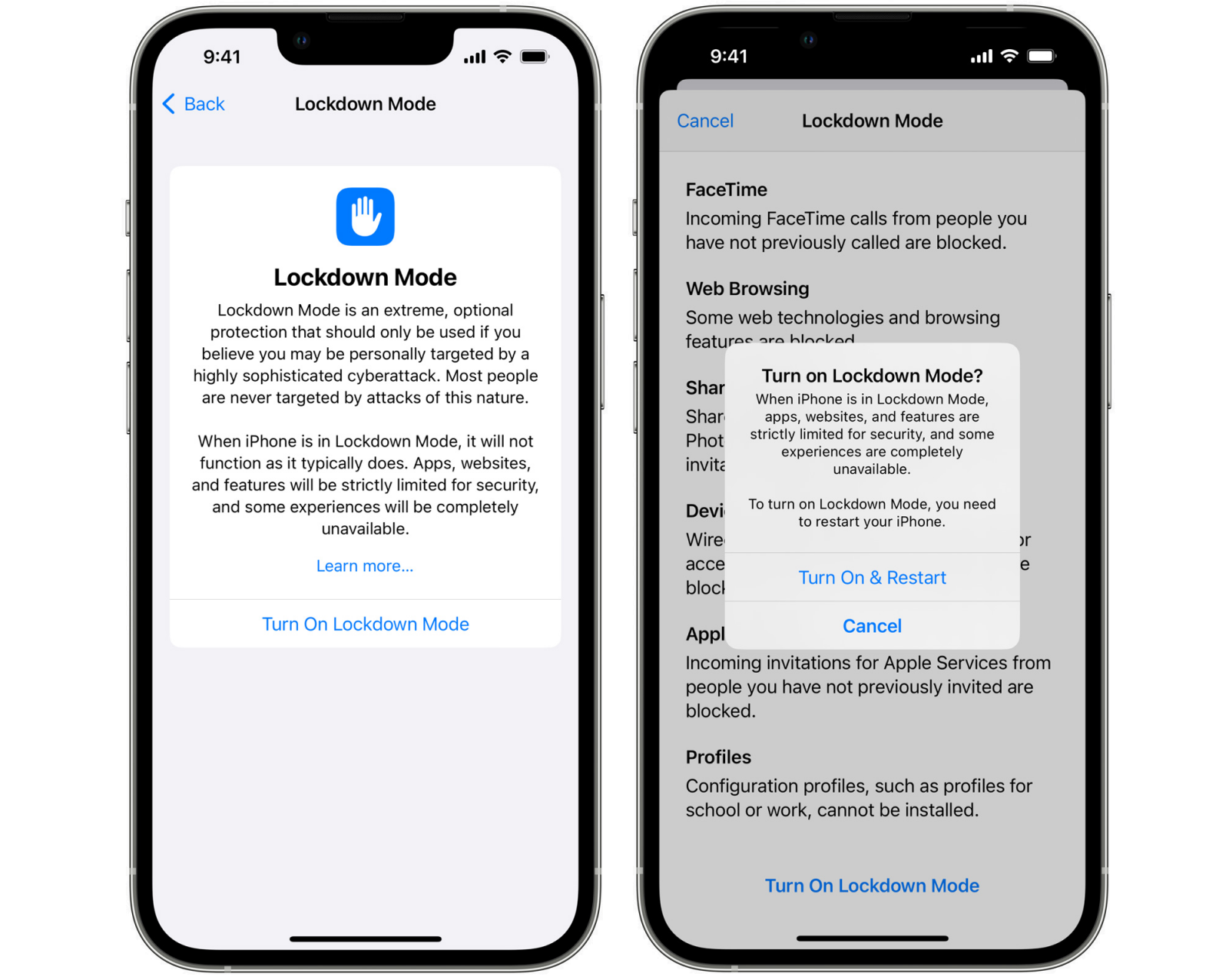
Apple announced that a new security feature known as Lockdown Mode will roll out with iOS 16, iPadOS 16, and macOS Ventura to protect high-risk individuals like human rights defenders, journalists, and dissidents against targeted spyware attacks.
Once enabled, the Lockdown Mode will provide Apple customers with messaging, web browsing, and connectivity protections designed to block mercenary spyware (like NSO Group's Pegasus) used by government-backed hackers to monitor their Apple devices after infecting them with malware.
Attackers' attempts to compromise Apple devices using zero-click exploits targeting messaging apps such as WhatsApp and Facetime or web browsers will get automatically blocked, seeing that vulnerable features like link previews will be disabled.
"Turning on Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura further hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware," Apple said.
The first version of Lockdown Mode will include protections for multiple operating systems features exposed to attacks, including:
- Messages: Most message attachment types other than images are blocked. Some features, like link previews, are disabled.
- Web browsing: Certain complex web technologies, like just-in-time (JIT) JavaScript compilation, are disabled unless the user excludes a trusted site from Lockdown Mode.
- Apple services: Incoming invitations and service requests, including FaceTime calls, are blocked if the user has not previously sent the initiator a call or request.
- Wired connections with a computer or accessory are blocked when iPhone is locked.
- Configuration profiles cannot be installed, and the device cannot enroll into mobile device management (MDM) while Lockdown Mode is turned on.
"To invite feedback and collaboration from the security research community, Apple has also established a new category within the Apple Security Bounty program to reward researchers who find Lockdown Mode bypasses and help improve its protections," Apple added.
"Bounties are doubled for qualifying findings in Lockdown Mode, up to a maximum of $2,000,000 — the highest maximum bounty payout in the industry."
Today's announcement came after Apple sued Pegasus spyware-maker NSO Group in November 2021 for the targeting and and spying of Apple users using NSO's surveillance tech.
Apple said at the time that state-sponsored attacks using NSO's spyware only targeted "a very small number" of individuals, across multiple platforms, including Android and Apple's iOS.
The attackers deployed NSO's surveillance software on the compromised devices of high-profile targets, including government officials, diplomats, dissidents, academics, and journalists worldwide.
Since December 2021, NSO Group spyware was also found deployed on iPhones belonging to Catalan politicians, journalists, and activists, Finnish diplomats, UK government employees, and U.S. Department of State employees.
The U.S. Commerce Department's Bureau of Industry and Security (BIS) also sanctioned NSO Group and three other companies from Israel, Russia, and Singapore in November for spyware development and selling hacking tools used by government-backed hacking groups.
"Lockdown Mode is a groundbreaking capability that reflects our unwavering commitment to protecting users from even the rarest, most sophisticated attacks," added Ivan Krstić, Apple’s head of Security Engineering and Architecture, on Wednesday.
"While the vast majority of users will never be the victims of highly targeted cyberattacks, we will work tirelessly to protect the small number of users who are."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now