Phishing attacks targeting Middle East countries double ahead of World Cup: report
Email-based phishing attacks targeting the Middle East doubled in October in the lead up to the World Cup in Qatar, according to new research from Trellix.
Many of the emails purport to come from the FIFA help desk or ticketing office while some impersonate specific team managers and departments. Others claim to be notifications about bans implemented by FIFA, or spoof Snoonu, the official food delivery partner of the World Cup.
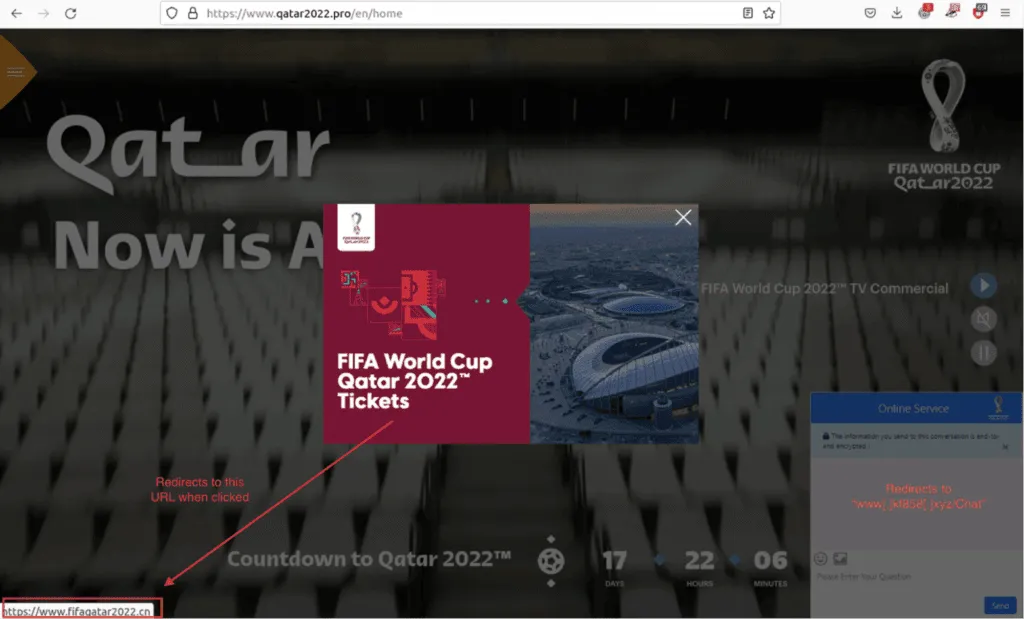
Trellix researchers said the campaigns leverage customized web pages that appeared very genuine and a variety of malwares were included in the attacks.
The goals of the cyberattacks include financial fraud, credential harvesting, data exfiltration, surveillance, and damage to a country or organization’s reputation.
Trellix provided a range of samples of the emails their researchers were seeing on a daily basis. One email impersonates David Firisua, the team manager for Auckland City FC, seeking confirmation of a payment made to FIFA. Many of the emails contain hyperlinks which take people to spoofed brand pages or phishing sites. Some of the emails pretend to be legal notices regarding unpaid fees to FIFA.
John Fokker, Head of Threat Intelligence & Principal Engineer at Trellix, told The Record that they anticipate these attacks to continue through January 2023.
“In this instance, we found the attention to the details incorporated into the malicious URLs and customized web pages to be notable, allowing cybercriminals to successfully impersonate league staff and team managers,” he explained.
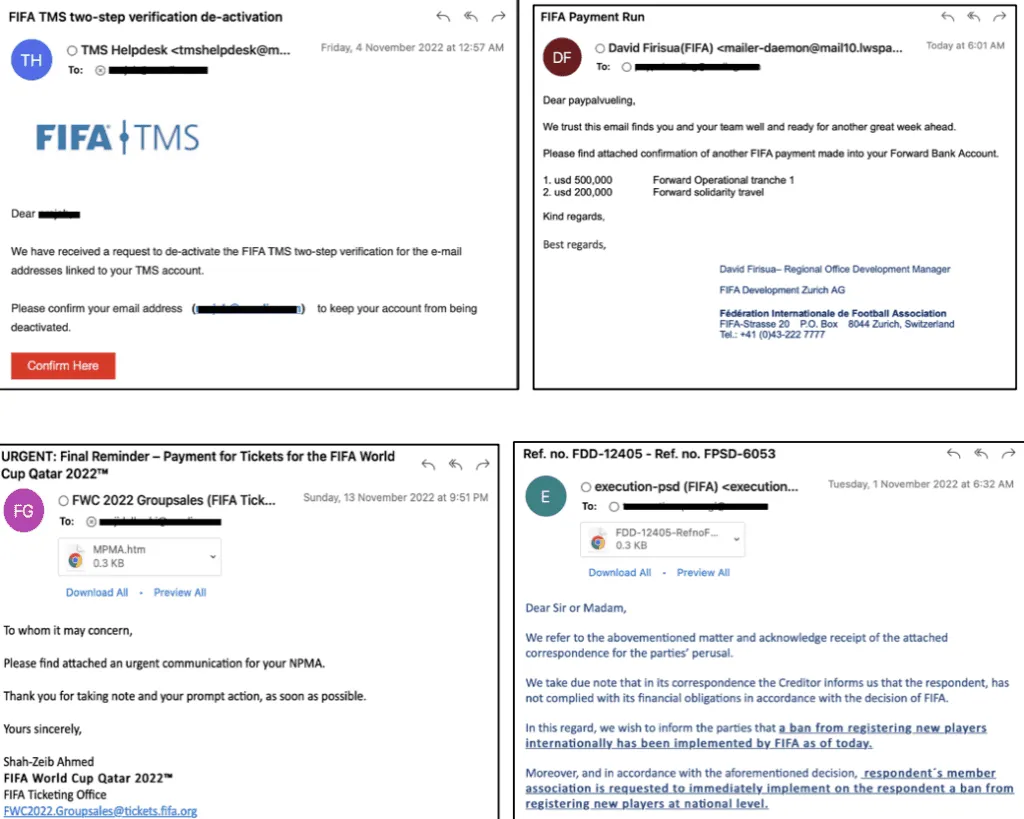
Trellix said the top five malware families it found targeting Middle Eastern countries right now included Qakbot, Emotet, Formbook, Remcos and QuadAgent.
The goal of most of the malware strains is to steal confidential data or information, credentials or gain remote control of a device.
Jeremy Fuchs, cybersecurity research analyst at Avanan, confirmed that they have also seen an influx of phishing emails related to the World Cup in a variety of different languages.
"One common thread is related to betting on the World Cup, trying to entice end-users to wager. Instead, the email and resulting link steals credentials," he said.
Daniel Clemens, CEO of cybersecurity firm ShadowDragon, told The Record that the cyber threat of the World Cup is not much different than those associated with any global event, like the Olympics.
“There is always a rise in phishing and activity related to these events. Holding the World Cup in Qatar has been a hot-button political issue since its announcement. The event offers more fodder and content for spammers and phishers,” he said.
But he noted that there are several other threats facing those attending or watching the event, including overreach by the Qatar government through mandatory apps downloaded by attendees.
Officials for the Dutch, German, French, and Norwegian governments have already told their citizens not to download Qatar's World Cup apps, Ehteraz and Hayya, over privacy concerns.
German officials went so far as to suggest that citizens bring essentially a burner phone that has none of their personal information and wipe the device after the World Cup ends.
“You wouldn’t give a stranger the keys to your house but phone apps can unknowingly harvest detailed, personal information about those who use them,” said Keeper Security CEO Darren Guccione.
“It’s particularly concerning when a nation state is collecting unauthorized information through an app, or worse yet, remotely accessing a device.”
Joseph Carson, chief security scientist and Advisory CISO at Delinea, told The Record that during all major events, such as the upcoming World Cup in Qatar, they always see a major increase in cybercrime targeting unsuspecting fans and followers.
Many fake, fraudulent websites, apps or emails that appear official will come loaded with an abundance of scams and these scams can result in stealing the victims credentials, passwords, credit card information, infecting their computer or smartphone with malicious software or even ransomware, Carson explained.
These can lead the unknowing victim to spread malware to family and friends, losing sensitive data or a major financial impact.
Cybersecurity firm Recorded Future, which owns The Record, released a report this week that said while no imminent state-sponsored cyber operations have been identified, Russia “is an outlier and very likely harbors a strong set of grievances and thus motivation for targeting the 2022 FIFA World Cup.”
Russia may want to “embarrass Qatar as the host country for siding with the coalition of countries supporting Ukraine’s territorial integrity, as well as to retaliate for Russia being banned from participating in the tournament.”
Russian military hackers were previously implicated in the Pyeongchang cyberattack that took place during the Olympics in February 2018, where Russian hackers deployed the OlympicDestroyer malware and damaged web servers during the opening ceremony.
In October 2020, the Justice Department indicted six Russian intelligence operatives for the attack on the Pyeongchang Games.
The report notes that large international sporting events are also attractive targets for financially motivated cybercriminals.
“Tournament-related phishing attacks use various lures such as so-called ticket giveaways, free streaming services to watch games, fake betting websites, and tournament-adjacent items like visas and travel, hotel, and restaurant bookings,” the researchers said.
“Other cybercriminal threats include, but are not limited to: fake mobile applications around the event that can distribute malware and harvest user data; sales on dark web markets and shops for counterfeit tickets and compromised credentials; and as above, ransomware attacks that would likely seek to opportunistically target victims based on accessibility, opportunity, and factors such as the ability to pay large ransom amounts.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

