
Hackers are launching new attacks to steal Steam credentials using a Browser-in-the-Browser phishing technique that is rising in popularity among threat actors.
The Browser-in-the-Browser technique is a trending attack method involving the creation of fake browser windows within the active window, making it appear as a sign-in pop-up page for a targeted login service.
In March 2022, BleepingComputer was the first to report on the capabilities of this new phishing kit created by security researcher mr.d0x. Using this phishing kit, threat actors create fake login forms for Steam, Microsoft, Google, and any other service.
Today, Group-IB published a new report on the topic, illustrating how a new campaign using the 'Browser-in-the-Browser' method targets Steam users, going after accounts for professional gamers.
These phishing attacks aim to sell access to those accounts, with some prominent Steam accounts valued between $100,000 and $300,000.
Baiting with tournament play
Group-IB reports that the phishing kit used in the observed Steam campaign isn't widely available in hacking forums or dark web markets. Instead, it is used privately by hackers that come together on Discord or Telegram channels to coordinate their attacks.
Prospective victims are targeted with direct messages on Steam, inviting them to join a team for LoL, CS, Dota 2, or PUBG tournaments.
The links the phishing actors share will bring the targets to a phishing site for what appears to be an organization sponsoring and hosting esports competitions.
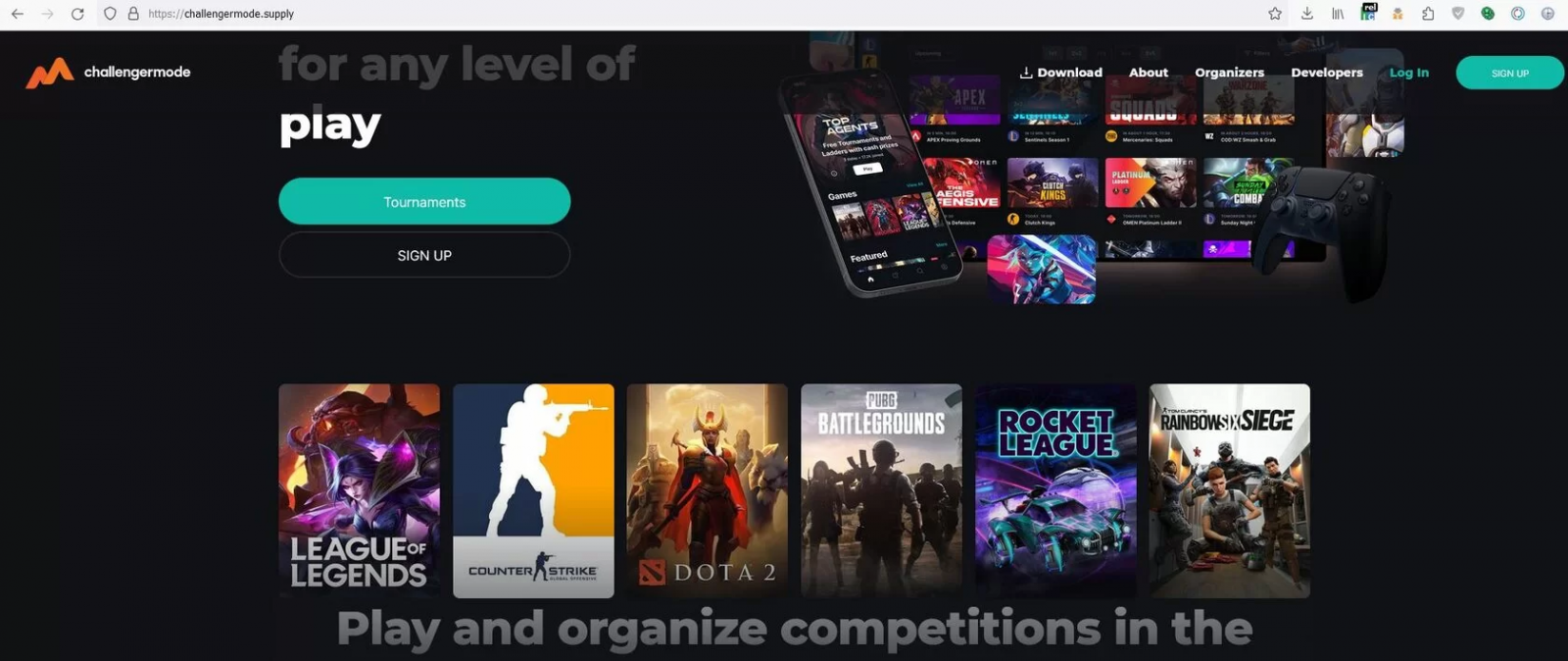
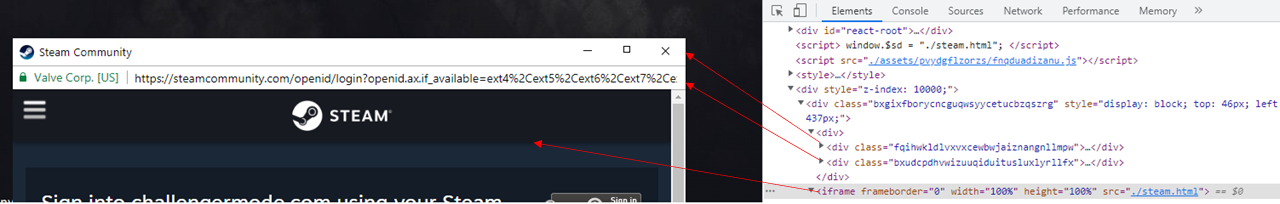
To join a team and play in a competition, the visitors are requested to log in via their Steam account. However, the new login page window isn't an actual browser window overlaid over the existing website but rather a fake window created within the current page, making it very hard to spot as a phishing attack.
The landing pages even support 27 languages, detecting the language from the victim's browser preferences and loading the correct one.
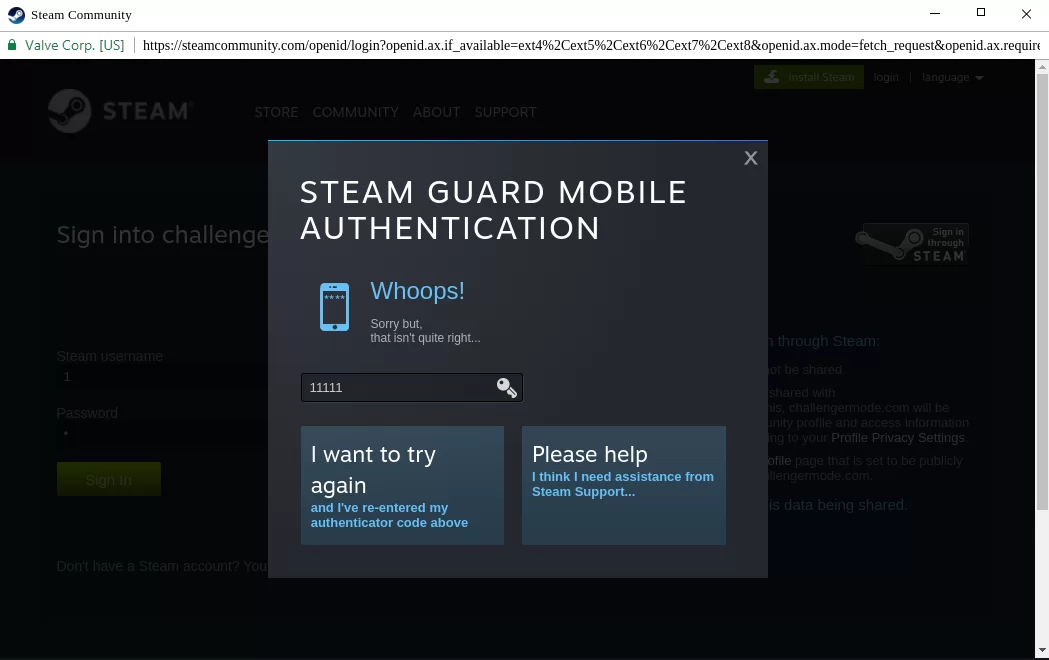
Once the victim enters their credentials, a new form prompts them to enter the 2FA code. If the second step is unsuccessful, an error message is displayed.
If the authentication is successful, the user is redirected to a URL specified by the C2, usually a legitimate address, to minimize the chances of the victim realizing the compromise.
At this point, the victim's credentials have already been stolen and sent to the threat actors. In similar attacks, the threat actors quickly hijack the Steam accounts, changing passwords and email addresses to make it more difficult for the victims to regain control over their accounts.
How to spot a Browser-in-the-Browser attack
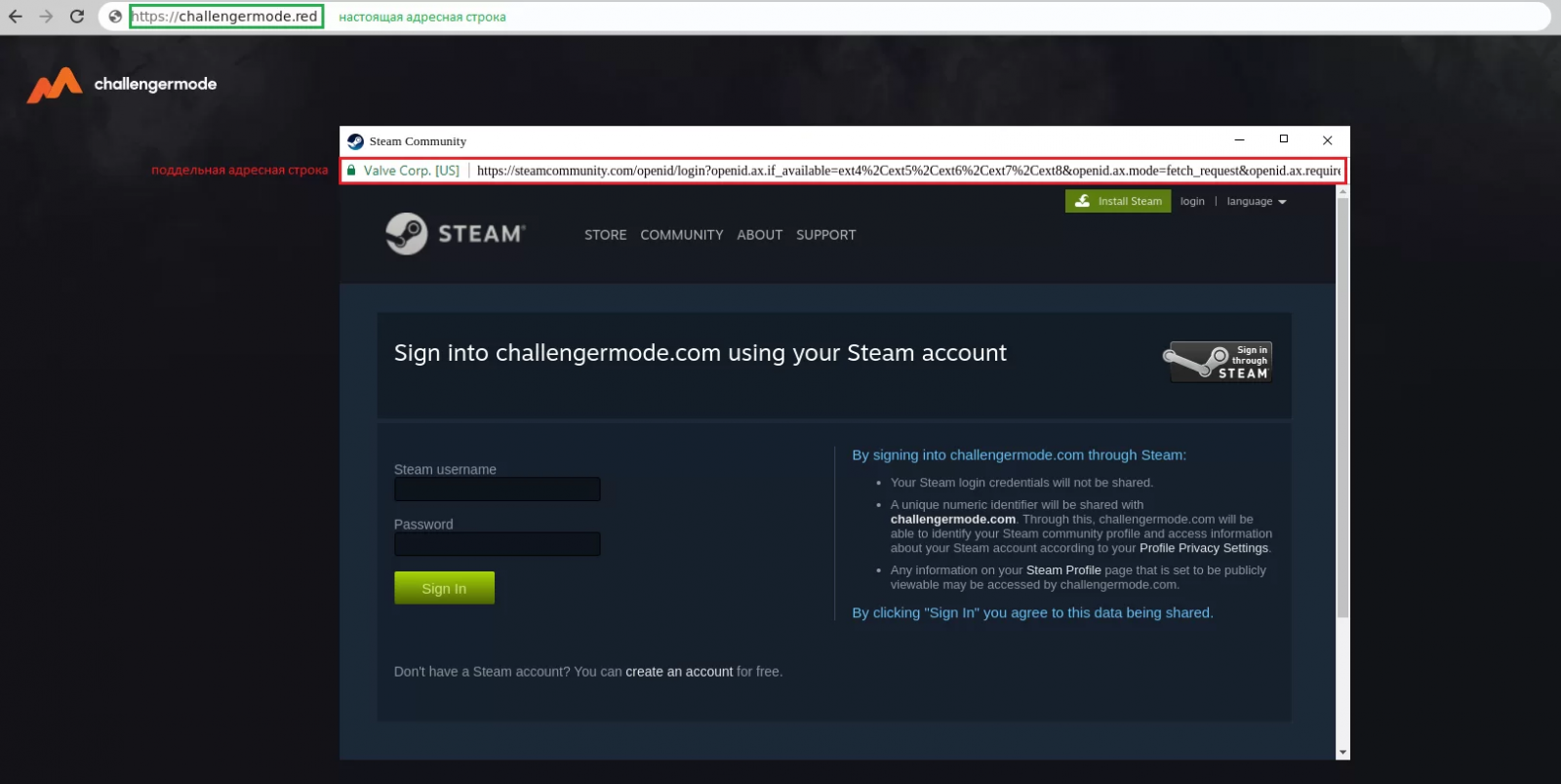
In all Browser-in-the-Browser phishing cases, the URL in the phishing window is the legitimate one, as the threat actors are free to display whatever they want since it's not a browser window but merely a render of one.
The same applies to the SSL certificate lock symbol, indicating an HTTPS connection, creating a false sense of security for the victims.
Even worse, the phishing kit allows users to drag the fake window around, minimize it, maximize it, and close it, making it very difficult to spot as a fake browser-in-the-browser window.
As the technique requires JavaScript, blocking JS scripts aggressively would prevent the fake login from being displayed. However, most people do not block scripts as it would break many popular websites.
The creator of the Browser-in-the-Browser toolkit, Mr.D0x, told BleepingComputer that the best method to check if a popup window is real is to try and move it past the original browser window.
"Always try to drag the popup window to the border of the browser. If it goes under the browsers borders then it's BiTB," explaines Mr.D0x.
Group-IB also shared the following ways to detect Browser-in-the-Browser attacks:
- Check if a new window is opened in the taskbar, assuming you ungroup programs in the Windows 10 taskbar. If no new taskbar window exists, then this is not a real window. Unfortunately, Windows 11 does not support ungrouping at this time.
- Try to resize the window. If you are unable to, it is likely a fake browser window.
- Fake BiTB browser windows will close if you minimize them.
In general, be very wary of direct messages received on Steam, Discord, or other game-related platforms, and avoid following links sent by users you do not know.
Update 9/13/22: Added further ways to detect Browser-in-the-Browser phishing attacks.
Update 9/20/22: A spokesperson of Challengermode has sent BleepingComputer the following comment:
The threat actors attempt to impersonate our legitimate service (challengermode.com) by registering similar domain names, which we are actively working to take down.
We would like to clarify that the real Challengermode platform uses valid Oauth2/OpenID flow that keeps user credentials private, and does not attempt to steal Steam accounts.


Comments
ArchPhoenixTeam - 1 year ago
Aren't we supposed to get a new icon on the task bar for the popup? I wouldn't trust that thing if I cannot open it's window individually and drag it to my second monitor.
fromFirefoxToVivaldi - 1 year ago
There are two ways in which this could be easily solved.
1. Browsers should drop the limited window functionality. Every popup should open in full browser tab. That way people would easily notice their addons missing, etc.
2. Valve could drop third-party authentication. Are there even any reasonable uses for that feature, aside from allowing companies to spy on the users' profiles?
RedDawn141 - 1 year ago
I got hit with this over three years ago, a little late to the game here, hu? Luckily I realized you could only sign in with steam, and didn't do it.