
Security researchers are warning that hackers can abuse online programming learning platforms to remotely launch cyberattacks, steal data, and scan for vulnerable devices, simply by using a web browser.
At least one such platform, known as DataCamp, allows threat actors to compile malicious tools, host or distribute malware, and connect to external services.
DataCamp provides integrated development environments (IDEs) to close to 10 million users that want to learn data science using various programming languages and technologies (R, Python, Shell, Excel, Git, SQL).
As part of the platform, DataCamp users gain access to their own personal workspace that includes an IDE for practicing and executing custom code, uploading files, and connecting to databases.
The IDE also allows users to import Python libraries, download and compile respositories, and then execute compiled programs. In other words, anything an industrious threat actor needs to launch a remote attack directly from within the DataCamp platform.
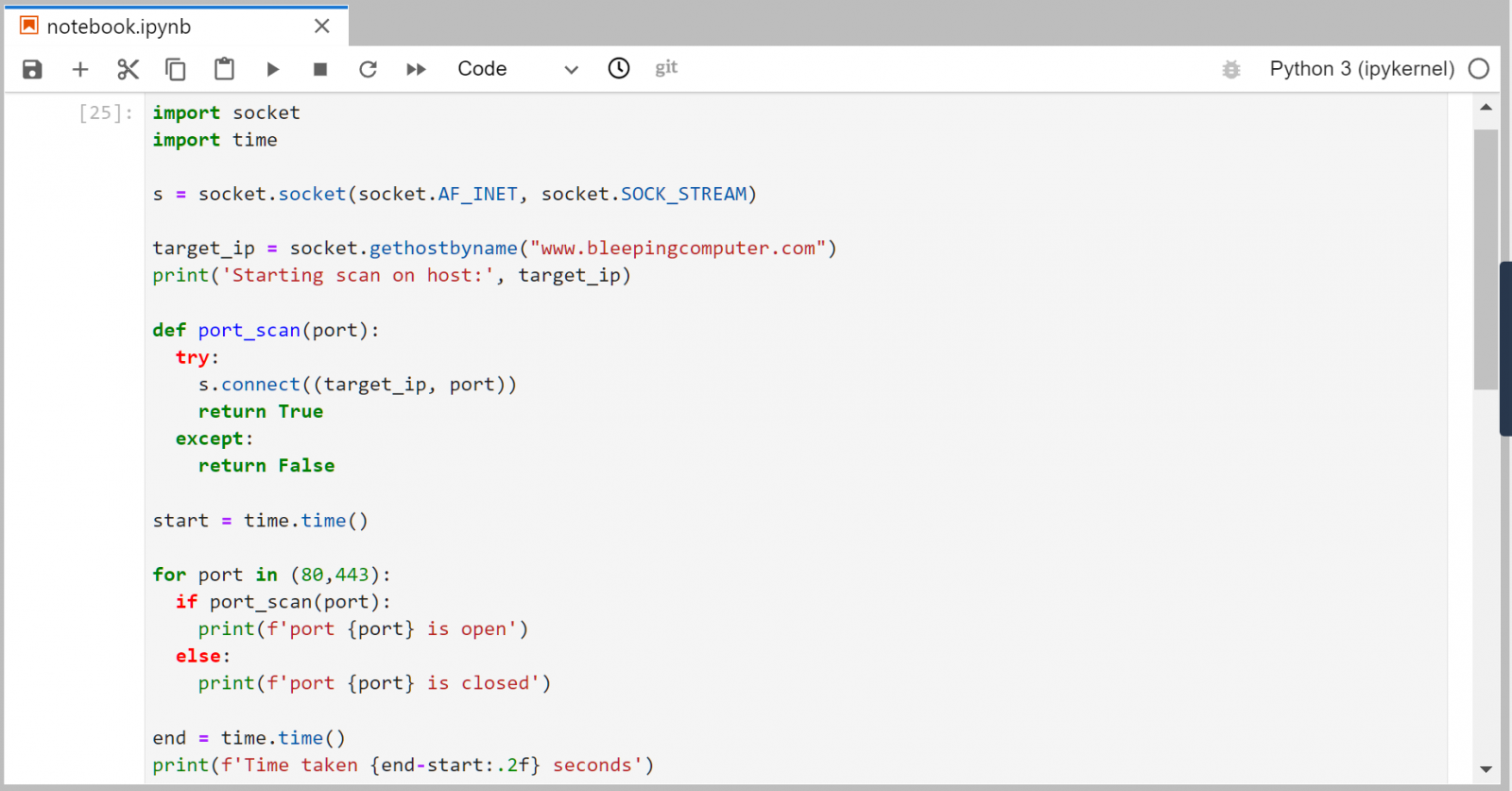
DataCamp open for abuse
After responding to an incident where a threat actor might have used DataCamp's resources to hide the origin of the attack, researchers at cybersecurity company Profero decided to investigate this scenario.
They found that DataCamp's advanced online Python IDE offered users the ability to install third-party modules that allowed connecting to an Amazon S3 storage bucket.
Omri Segev Moyal, CEO at Profero, says in a report shared with BleepingComputer that they tried this scenario on the DataCamp platform and were able to access an S3 bucket and exfiltrate all files to the workspace environment on the platform's website.
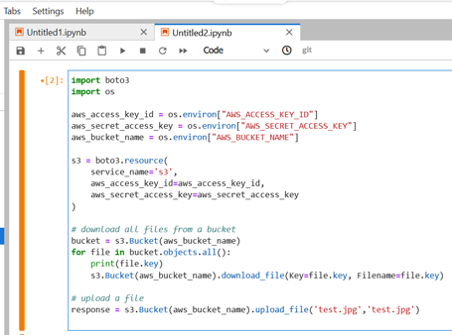
The researcher says that the activity coming from DataCamp is likely to pass by undetected and "even those who further inspect the connection would hit a dead end because there is no known definitive source listing the IP range of Datacamp."
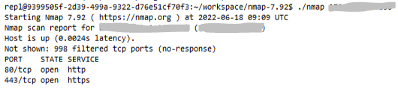
The investigation into this attack scenario went further and the researchers tried to import or install tools typically used in a cyberattack, such as the Nmap network mapping tool.
It was not possible to install Nmap directly but DataCamp allowed compiling it and executing the binary from the compilation directory.
Profero's Incident Response Team also tested if they could upload files using a terminal and get a link to share them. They were able to upload EICAR - the standard file for testing detection from antivirus solutions, and get a link for distributing it.
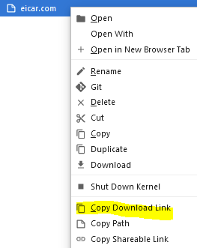
Profero's report today notes that the download link could be used to download additional malware to an infected system by using a simple web request.
Furthermore, these download links can be abused in other types of attacks, such as hosting malware for phishing attacks, or by malware to download additional payloads.
Inherent risk
BleepingComputer reached out to DataCamp for comment about Profero's research and a spokesperson said that "there is inherently a risk that some individuals may attempt to abuse our systems" because the platform provides "a live computing environment."
DataCamp states in their Terms of Service that abusing the platform is forbidden but threat actors are not the users to respect the rules.
DataCamp said that they "have taken reasonable measures" to prevent abuse from impacting other users on the platform and that they are monitoring their systems for misbehavior.
"In addition, in order to prevent individual malpractice, we have implemented a responsible disclosure policy and monitor our systems on an ongoing basis to mitigate risk" - DataCamp
Abuse likely possible on other platforms
Although Profero did not extend their research to other learning platforms, the researchers believe that DataCamp is not the only one that hackers could abuse.
Another platform that provides a terminal is Binder, a project running on an open infrastructure that is managed by volunteers. The service makes repositories hosted on other infrastructures (GitHub, GitLab) available to users through their browser.
A representative from the project told BleepingComputer that the BinderHub instance they deploy "implements several safeguards to limit how it could be used in an attack chain."
The restrictions apply to resources that can be used, bandwidth, and blocking potentially malicious applications.
The Binder representative said that they are willing to add more safeguards in the BinderHub source code if Profero's report shows that further steps are necessary.
Profero encourages providers of online code learning platforms to keep a list of outgoing customer traffic gateways and make it publicly accessible so that defenders can locate the origin of an attack, should it be the case.
The company's recommendation also includes implementing a safe and easy way for users to submit abuse reports.


Comments
Icepop33 - 1 year ago
Vector, vectors everywhere.
Like any tool, an online IDE can be used for ill or good.
I don't think the answer is taking away our toys; it's awareness and education.
I think keeping traffic logs is a sensible solution to this issue and hopefully they do it voluntarily and it becomes standard procedure in the ToS.
If you want to remain anonymous while launching a cyber attack, there are certainly other ways (not judging lol), but it's a bad look for an ostensibly legit organization to be enabling script kiddies at scale.
Thank you for the article.