
LinkedIn is holding the top spot for the most impersonated brand in phishing campaigns observed during the second quarter of 2022.
Statistical data from cybersecurity company Check Point shows that the social platform for professionals is at the top of the list for the second quarter in a row.
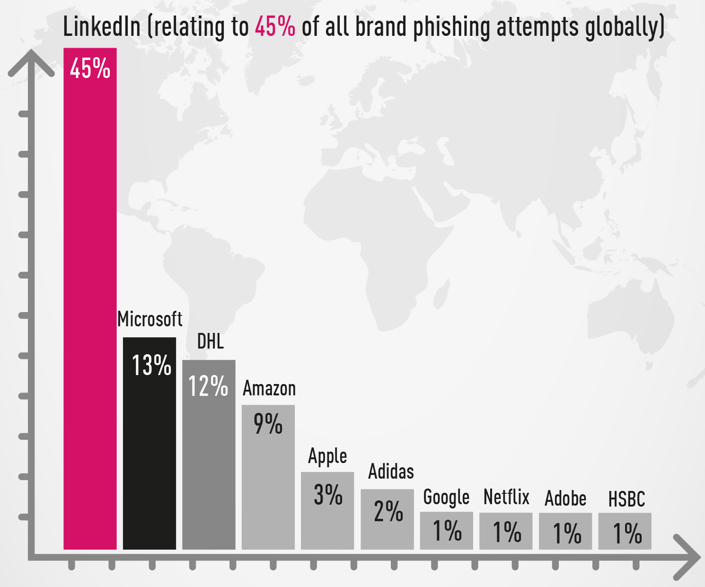
Compared to the first quarter of the year, LinkedIn impersonation dropped from 52% to 45%. However, it maintains a considerable distance from the second most imitated brand by fraudsters, Microsoft, currently at 13%.
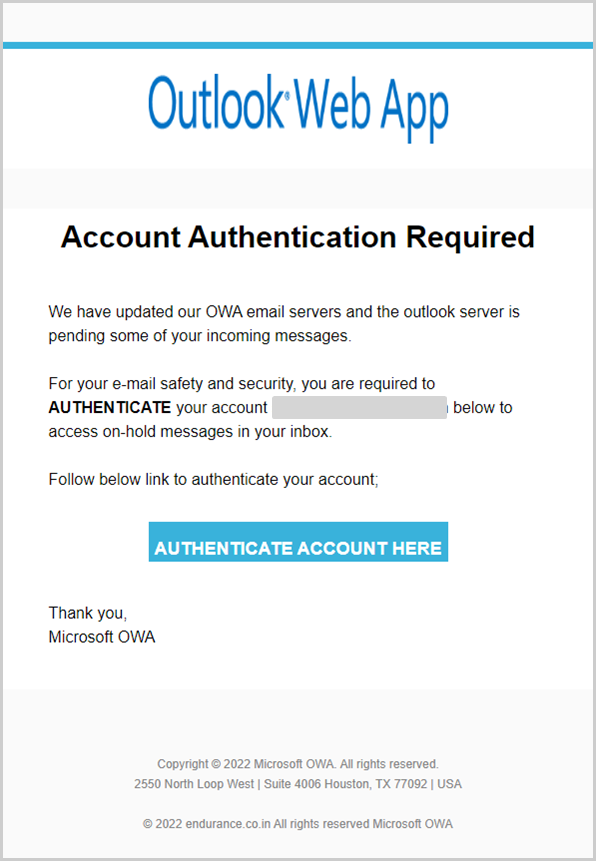
The central theme in spoofed Microsoft emails is requests to verify Outlook accounts to steal usernames and passwords.
(Check Point)
DHL currently holds the third spot in the list with 12%, down from 14%.
Amazon rose to the fourth position, jumping from 2% in Q1 2022 to 9% this quarter, while Apple follows on fifth place with 3%; also a notable increase compared to last quarter’s 0.8%.
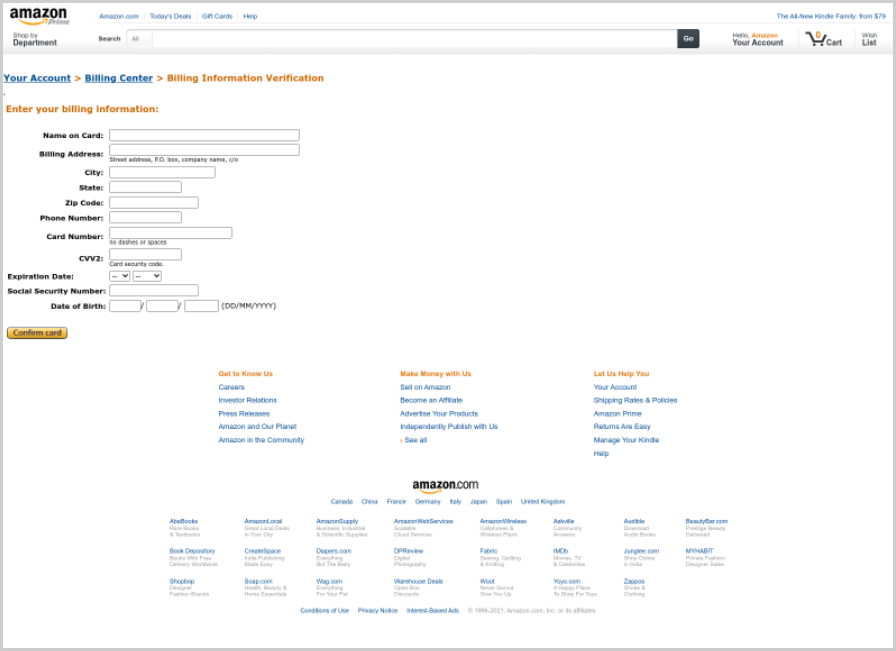
In the case of Amazon, the phishing emails attempt to steal the target’s billing information, including full credit card data, the researchers say.
LinkedIn phishing
As Check Point explains in its report, phishing campaigns using fake LinkedIn emails try to mimic common messages from the platform to its users, such as “You appeared in 8 searchers this week”, or “You have one new message.”
The sender addresses are spoofed to appear as if the messages are automated or come from the support or even the security department.
Some lures used in these campaigns include fake promotions for the LinkedIn Pro service, bogus policy updates, or even threats of account termination for “unverified customers.”
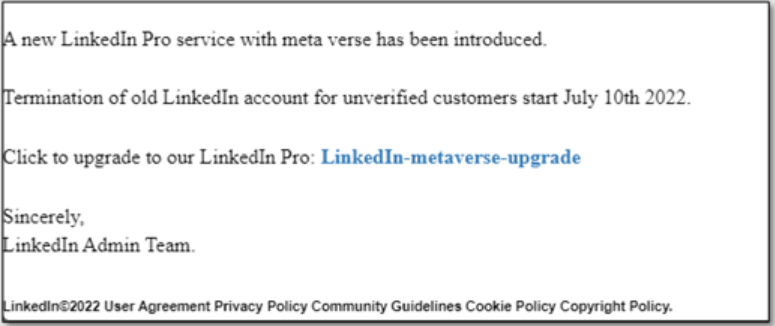
They all lead to a phishing web page where the victims are asked to enter their LinkedIn credentials, enabling the threat actors to take over the accounts.
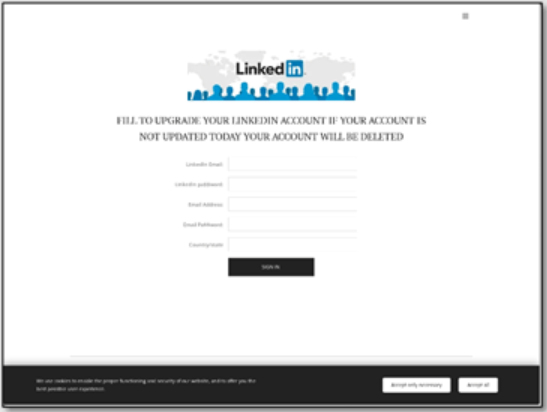
With access to a LinkedIn account, a threat actor could deploy targeted phishing campaigns to reach the victim's coworkers or valuable individuals in their connections network.
Another reason for targeting LinkedIn accounts is that they can be used to set up fake job offer campaigns. In a recent example, North Korean hackers were able to trick an employee of a token-based online video game into downloading a malicious PDF that allowed the threat actor to steal $620 million worth of cryptocurrency.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now