
A threat actor is selling on a Russian-speaking hacking forum what they claim to be hundreds of gigabytes of data allegedly stolen from U.S. Marshals Service (USMS) servers.
USMS is a Justice Department bureau that provides support to the federal justice system by executing federal court orders, assuring the safety of government witnesses and their families, seizing illegally obtained assets, and more.
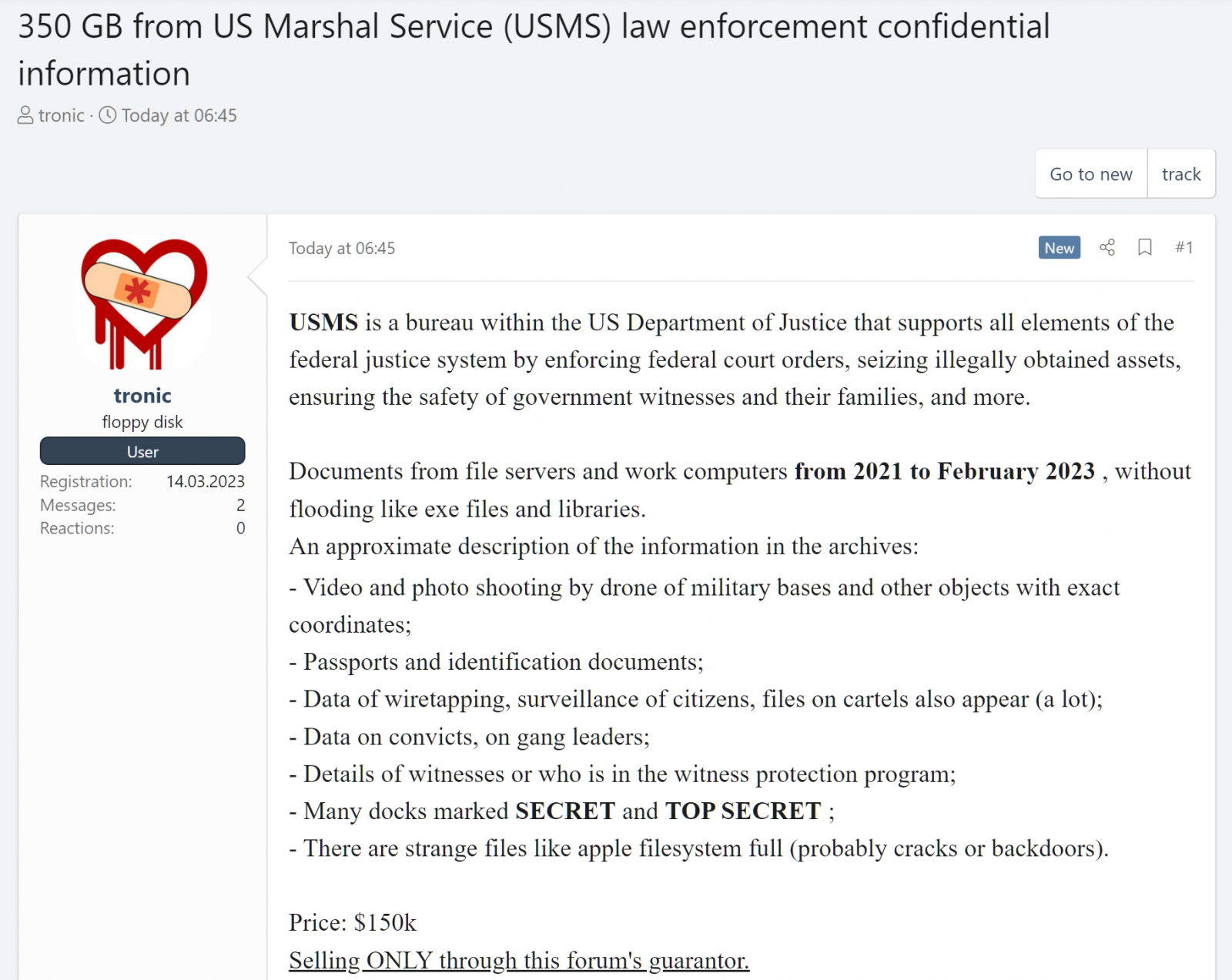
The announcement, titled "350 GB from US Marshal Service (USMS) law enforcement confidential information," was added earlier today using an account registered yesterday afternoon.
According to the seller, the database is being sold for $150,000 and contains "documents from file servers and work computers from 2021 to February 2023, without flooding like exe files and libraries," according to the seller.
The information includes aerial footage and photos of military bases and other high-security areas, copies of passports and identification documents, and details on wiretapping and surveillance of citizens.
The files also contain information on convicts, gang leaders, and cartels. The threat actor also claims that some files are marked as SECRET or TOP SECRET.
The threat actor also claims the database includes details about witnesses in the witness protection program.
A USMS spokesperson was not available for comment when contacted by BleepingComputer today for a statement regarding the claims that data stolen in last month's incident is now up for sale.
USMS investigating a ransomware attack
This comes after the USMS confirmed last month that it's investigating a "data exfiltration event" after a February 17 ransomware attack that impacted what it described as "a stand-alone USMS system."
According to USMS spokesperson Drew Wade, the data stolen in this incident, tagged as a "major incident," includes USMS employees' personally identifiable information.
"The affected system contains law enforcement sensitive information, including returns from legal process, administrative information, and personally identifiable information pertaining to subjects of USMS investigations, third parties, and certain USMS employees," Wade said.
However, sources close to the incident told NBC News that the attackers didn't gain access to USMS' Witness Security Files Information System (also known as WITSEC or the witness protection program) database.
USMS disclosed another data breach in May 2020 after it exposed the details of more than 387,000 former and current inmates in a December 2019 incident, including their names, dates of birth, home addresses, and social security numbers.
The U.S. Federal Bureau of Investigation (FBI) also disclosed a cybersecurity incident two weeks ago, described as a now-contained "isolated incident."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now