
American fast food chain Chick-fil-A has confirmed that over 71,000 customers' accounts were breached in a months-long credential stuffing attack, allowing threat actors to use stored rewards balances and access personal information.
In January, BleepingComputer reported that Chick-fil-A had begun investigating what it described as "suspicious activity" on customers' accounts.

At the time, Chick-fil-A set up a support page with information on what customers should do if they detect suspicious activity on their accounts.
This warning came after BleepingComputer emailed Chick-fil-A before Christmas about reports of Chick-fil-A user accounts being stolen in credential-stuffing attacks and sold online.
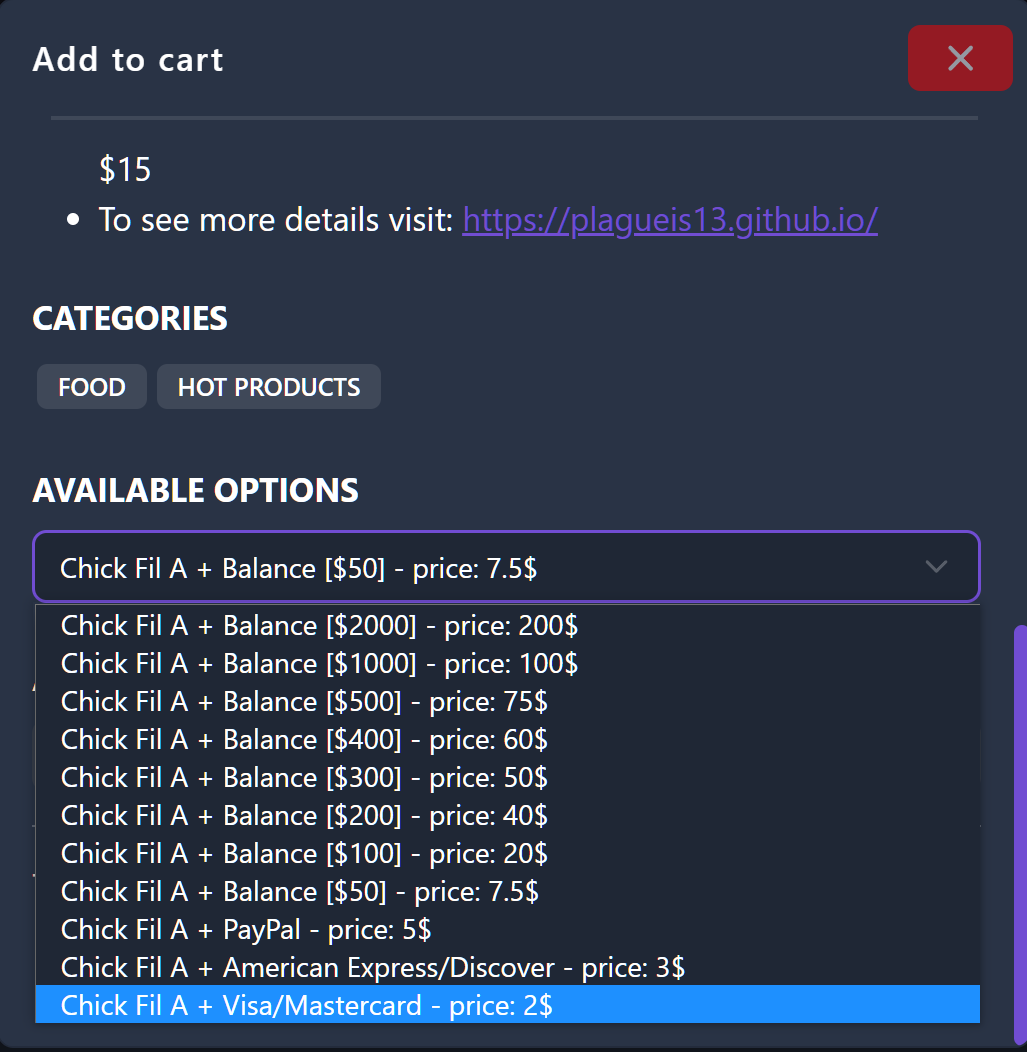
These accounts were sold for prices ranging from $2 to $200, depending on the rewards account balance and linked payment methods.
One Telegram channel seen by BleepingComputer showed people purchasing these accounts and then sharing pictures of their purchases made through these accounts.
Source: BleepingComputer
Chick-fil-A confirms credential stuffing attack
Today, Chick-fil-A confirmed our reporting in a security notice submitted to multiple Attorney General offices, stating that they suffered a credential stuffing attack between December 18th, 2022, and February 12th, 2023. This sustained attack allowed the threat actors to hack a total of 71,473 Chick-fil-A accounts.
"Following a careful investigation, we determined that unauthorized parties launched an automated attack against our website and mobile application between December 18, 2022 and February 12, 2023 using account credentials (e.g., email addresses and passwords) obtained from a third-party source.
Based on our investigation, we determined on February 12, 2023 that the unauthorized parties subsequently accessed information in your Chick-fil-A One account." - Chick-fil-A notification.
The fast food chain is warning impacted customers that threat actors who accessed their account would have also had access to their personal information, including their name, email address, Chick-fil-A One membership number and mobile pay number, QR code, masked credit/debit card number, and the amount of Chick-fil-A credit (e.g., e-gift card balance) on your account (if any).
For some customers, the information may have included birthdays, phone numbers, physical addresses, and the last four digits of credit cards.
In response to the attack, Chick-fil-A forced customers to reset passwords, froze funds loaded into accounts, and removed any stored payment information from accounts.
Chick-fil-A also states that they restored Chick-fil-A One account balances and added rewards to impacted accounts as a way of apologizing.
As the accounts were breached using credentials exposed in other data breaches, impacted users must change their passwords at all sites they frequent, especially if they use the same Chick-fil-A password.
When resetting passwords, use a unique password for each site and store them in a password manager, like Bitwarden, so that they can be easily managed.
While there is no evidence that personal information was abused, impacted customers should also be on the lookout for potentially targeted phishing emails utilizing this information.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now