
Russian hackers have been targeting Ukrainian entities with previously unseen info-stealing malware during a new espionage campaign that is still active.
Security researchers at Cisco Talos attribute the campaign to Gamaredon, a Russian state-backed threat group with a long history of targeting mainly organizations in the Ukrainian government, critical infrastructure, defense, security, and law enforcement.
Also known as Primitive Bear, Shuckworm, IronTiden, and Callisto, Gamaredon relies on social engineering and spear phishing to establish long-term access to victim systems.
New malware in Gamaredon’s toolkit
The threat group is known for developing malware (e.g. malicious scripts, info stealers, backdoors) that is used exclusively in its campaigns.
Cisco Talos attributed a newly observed espionage campaign (August 2022) to Gamaredon and noticed the use of a new info stealer that can extract from victim computers specific file types as well as deploy additional malware.
“This is a new infostealer that Gamaredon has not previously used in other campaigns. We suspect it may be a component of Gamaredon’s “Giddome'' backdoor family, but we are unable to confirm that at this time” - Cisco Talos
The new piece of malware has clear instructions to steal files with the following extensions: .DOC, .DOCX, .XLS, .RTF, .ODT, .TXT, .JPG, .JPEG, .PDF, .PS1, .RAR, .ZIP, .7Z AND .MDB.
It is delivered by a PowerShell script that is similar to one described in a recent alert from the Ukraine CERT about Gamaredon intrusions during the first half of the year.
Cisco Talos says that Gamaredon’s new infostealer can exfiltrate files from attached storage devices (local and remote), making for each stolen file a POST request with metadata and its content.
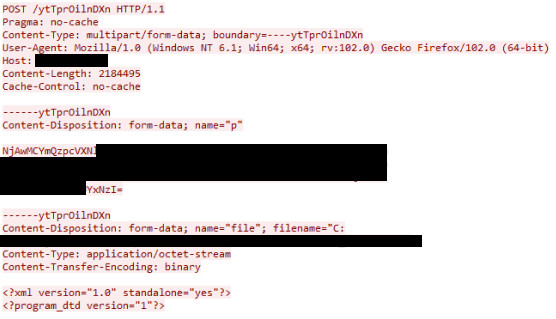
source: Cisco Talos
During the recursive enumeration of all files in directories, the malware avoids system folders to focus only on files of interest to the threat actor.
The researchers noticed that the infostealer can also download additional files from the command and control (C2) server, which delivers instructions on how the delivered data should be treated.
If the payload is an executable (flagged with “1”), the file is written to disk and run. An alternative is a VBS file (flagged with “2”), which is also written to disk and launched using Windows Script Host (wscript.Exe).
A third option is a blob of data, which is flagged with any other value than “1” or “2” and gets stored in the Windows temporary folder.
Cisco Talos notes that an indication of Gamaredon’s malware being present on the system is a registry key called “Windows Task“ to run at logon, and a mutex named ”Global\flashupdate_r.“
Gamaredon’s infostealer has been added to the Virus Total database about a little over a month ago and is currently detected by at least 50 antivirus engines.
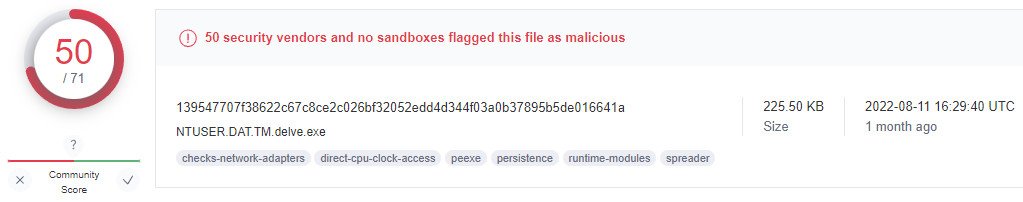
source: Cisco Talos
The hackers deliver the malware through phishing emails that carry Microsoft Office documents with malicious VBS macros.
The VBS code is hidden in remote templates and executed when opening the document, downloading RAR archives with LNK files.
Both LNK files and Microsoft Office documents have names referring to the Russian invasion of Ukraine.

source: Cisco Talos
The purpose of LNK files is to run mshta.exe to download and parse a remote XML that executes a malicious PowerShell script from a Russian domain (xsph[.]ru) that Gamaredon has used for past espionage campaigns.
Another PowerShell script is downloaded and executed to collect data (computer name, volume serial number, base64-encoded screenshot) from the victim and send it to a remote server.
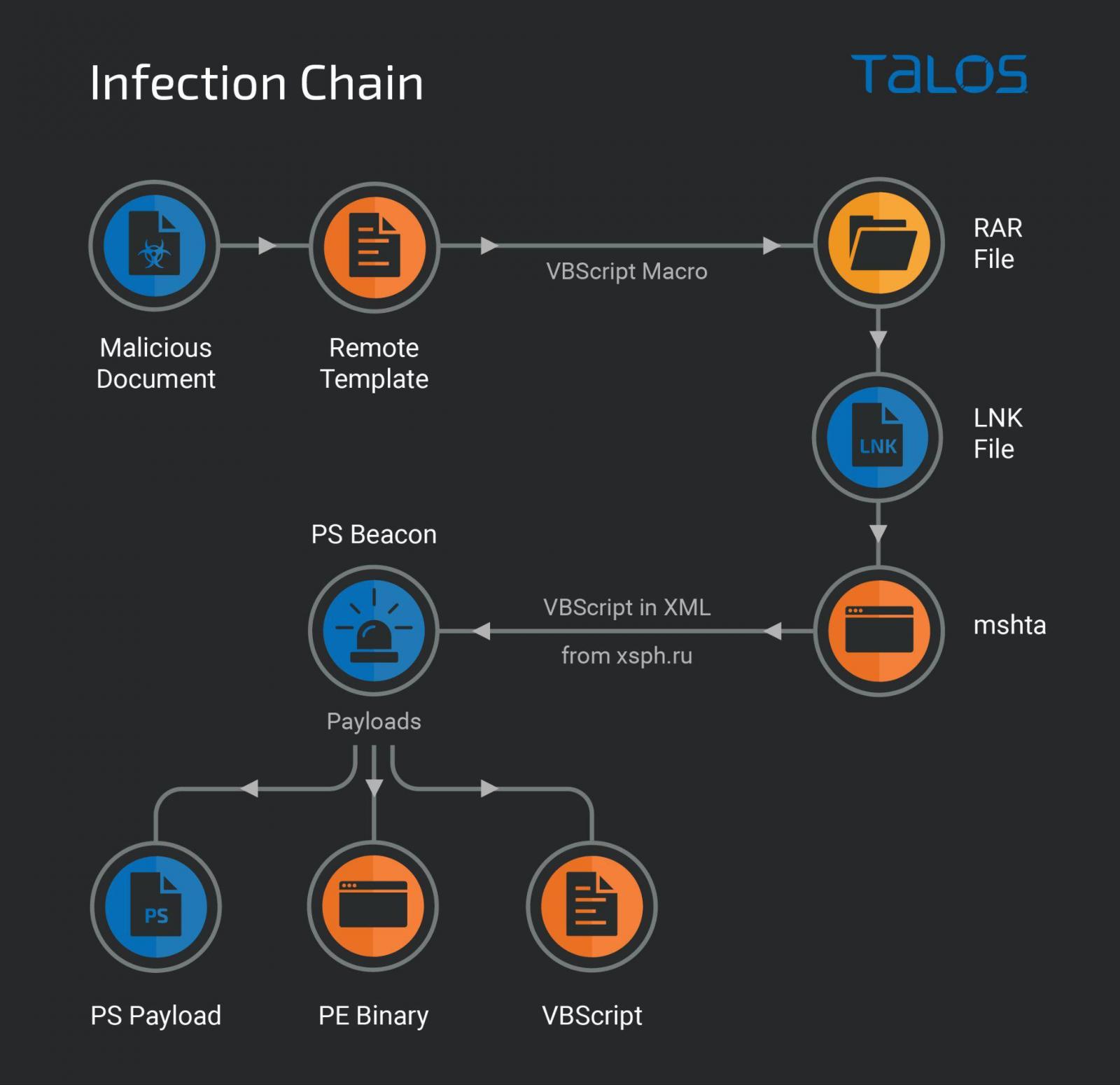
source: Cisco Talos
Cisco Talos has provided a list of indicators of compromise for malicious documents, LNK files, RAR archives, the new infostealer, URLs, and payload drop sites.
Organizations can use the IoCs to defend their organizations from espionage campaigns Gamaredon may deploy.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now