
Lending protocol Euler Finance was hit by a cryptocurrency flash loan attack on Sunday, with the threat actor stealing $197 million in multiple digital assets.
The cryptocurrency theft involved multiple tokens, including $8.75 million worth of DAI, $18.5 million in WBTC, $33.85 million in USDC, and $135.8 million in stETH.
The attacker's ETH wallet used to store the stolen funds is being tracked, so it will be challenging for the perpetrator to move the stolen funds around and convert them to a usable form.
However, Elliptic reports that the threat actors are already laundering the proceeds through the sanctioned cryptocurrency mixer Tornado Cash.
The startup behind Euler Finance, UK-based Euler Labs, shared a brief statement on Twitter, saying that they are currently engaging with security professionals and law enforcement agencies and will release more information when ready.
The attack caused the Euler (EUL) token value to drop by 44.2% overnight, going from $6.56 to $3.37 when writing this.
Flash loan attacks exploit a vulnerability in a lending protocol to borrow a large sum of money without having to return its value to the service.
The attackers use an exploit that allows them to manipulate the price of a token or asset on the platform during the few seconds that they hold the lent amount, so when the trade is complete, they are left with a massive profit.
A similar flash loan attack targeted the Beanstalk DeFi platform in April 2022, when threat actors stole $182 million in assets.
Blockchain security and analytics company PeckShield reported that the hack of Euler was made possible due to the flawed logic in its donation and liquidation system.
More specifically, the function “donateToReserves” did not verify that the attacker was donating an over-collateralized sum, and the liquidation system did not correctly verify the conversion rate from the borrowed to the collateral asset.
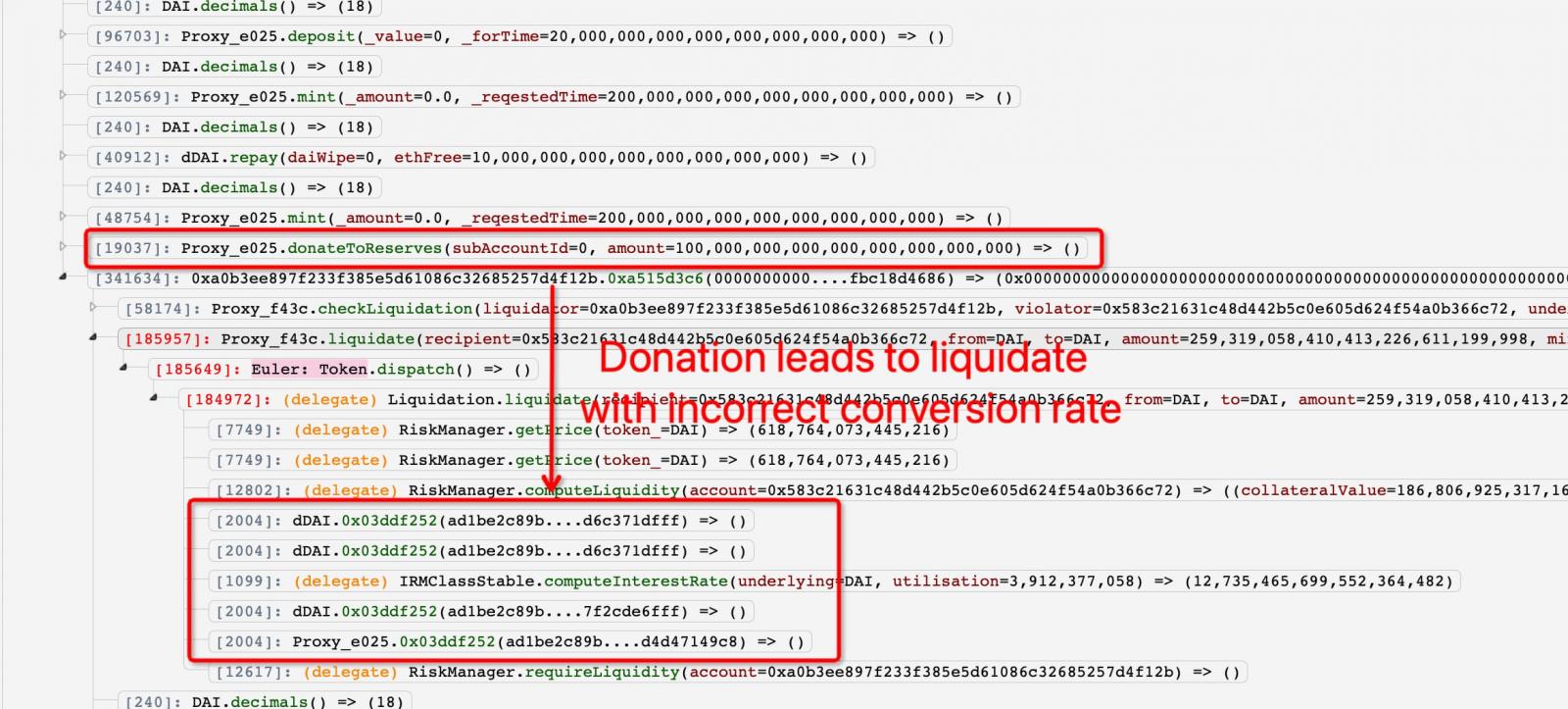
These flaws allowed the attackers to manipulate the conversion rate to profit from the liquidation process.
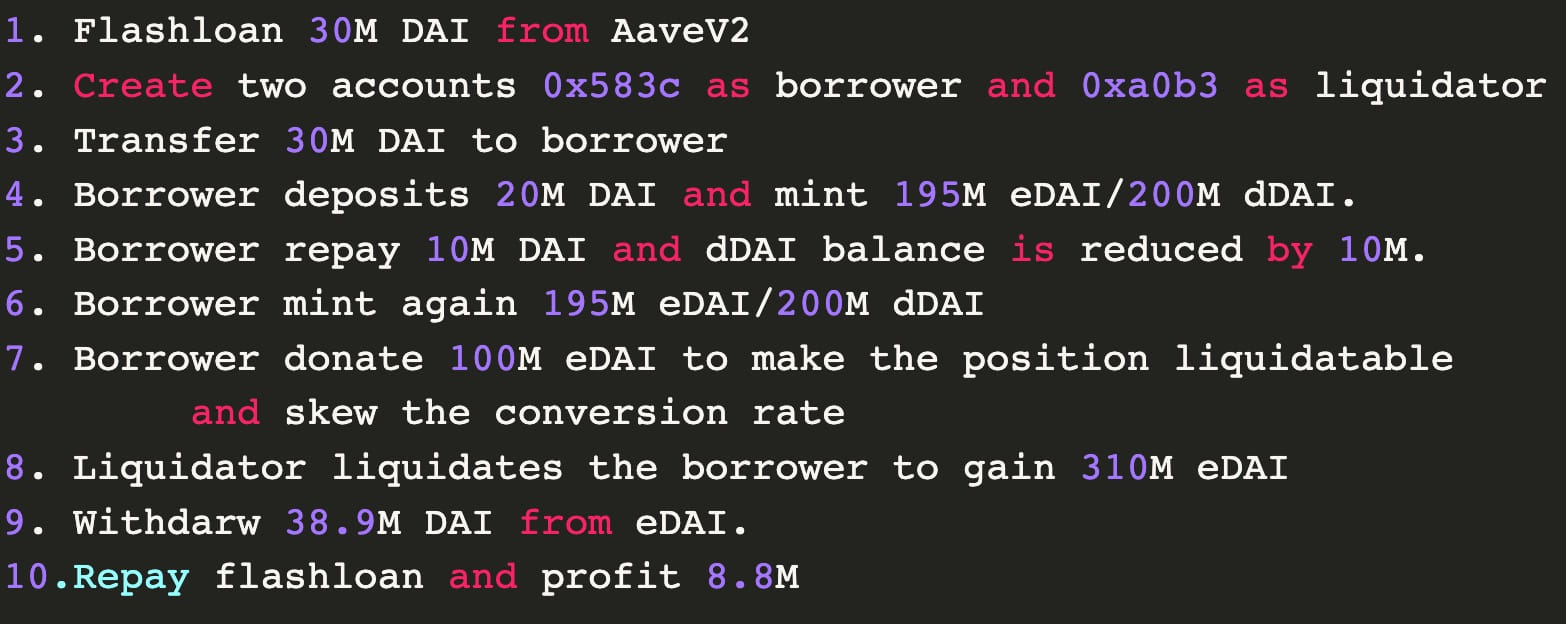
PeckShield says the attack involved two hackers, a borrower and a liquidator, working in coordination to perform the required actions illustrated in the below diagram.
DeFi hacks have been rising in the past couple of years, with hackers abandoning their efforts to attack exchanges and shifting their focus to the rapid exploitation of logic flaws in crypto lending platform's smart contracts.
These attacks are so devastating that they can derail overnight a healthy and prosperous company that has already undergone multiple security audits.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now