
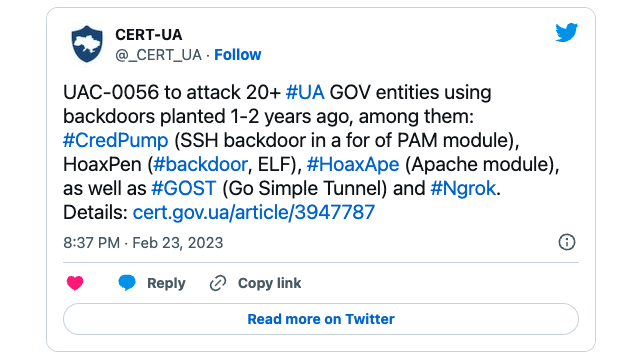
The Computer Emergency Response Team of Ukraine (CERT-UA) says Russian state hackers have breached multiple government websites this week using backdoors planted as far back as December 2021.
CERT-UA spotted the attacks after discovering a web shell on Thursday morning on one of the hacked websites that the threat actors (tracked as UAC-0056, Ember Bear, or Lorec53) used to install additional malware.
This web shell was created in December 2021 and was used to deploy CredPump, HoaxPen, and HoaxApe backdoors one year ago, in February 2022, according to CERT-UA.
The threat actors also used the GOST (Go Simple Tunnel) and the Ngrok tools during the early stages of their attack to deploy the HoaxPen backdoor.
"Today, on February 23, an attack was detected on a number of websites of Ukrainian central and local authorities, resulting in a modification of the content of some of their webpages," Ukraine's cybersecurity defense and security agency SSSCIP said on Thursday.
"Presently, in the framework of the United Response Team under the National Cybersecurity Coordination Center, experts from the SSSCIP, the Security Service of Ukraine and the Cyber Police are working together to isolate and investigate the cyber incident.
SSSCIP added that the incident had not caused "essential system failures or disruptions" that would affect the operation of Ukrainian public authorities.
Ember Bear, the group behind this week's incident, has been active since at least March 2021 and is focused on targeting Ukrainian entities with backdoors, information stealers, and fake ransomware primarily delivered via phishing emails.
However, its operators are also suspected of orchestrating attacks against North American and Western European organizations.
The APT group was spotted ramping up its phishing campaigns and network compromise efforts in Ukraine starting in December 2021.
They were also spotted targeting Georgian government agencies with phishing emails, and their attacks have demonstrated coordination and alignment with Russian state interests.
Last month, CERT-UA disclosed another cyberattack linked to the Russian Sandworm military hacking group against the country's national news agency (Ukrinform) with CaddyWiper data-wiping malware, which failed to impact its operations.
The same group used CaddyWiper malware in another failed attack from April 2022 against a large Ukrainian energy provider.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now