
A business email compromise (BEC) group named 'Crimson Kingsnake' has emerged, impersonating well-known international law firms to trick recipients into approving overdue invoice payments.
The threat actors impersonate lawyers who are sending invoices for overdue payment of services supposedly provided to the recipient firm a year ago.
This approach creates a solid basis for the BEC attack, as recipients may be intimidated when receiving emails from large law firms like the ones impersonated in the scams.
Impersonating law firms
Analysts at Abnormal Security, who first discovered Crimson Kingsnake activity in March 2022, report having identified 92 domains linked to the threat actor, all similar to genuine law firm sites.
This typosquatting approach enables the BEC actors to send out emails to victims via an address that appears authentic at first glance.
The emails contain the logos and letterheads of the impersonated entities and are crafted professionally, featuring punctual writing.
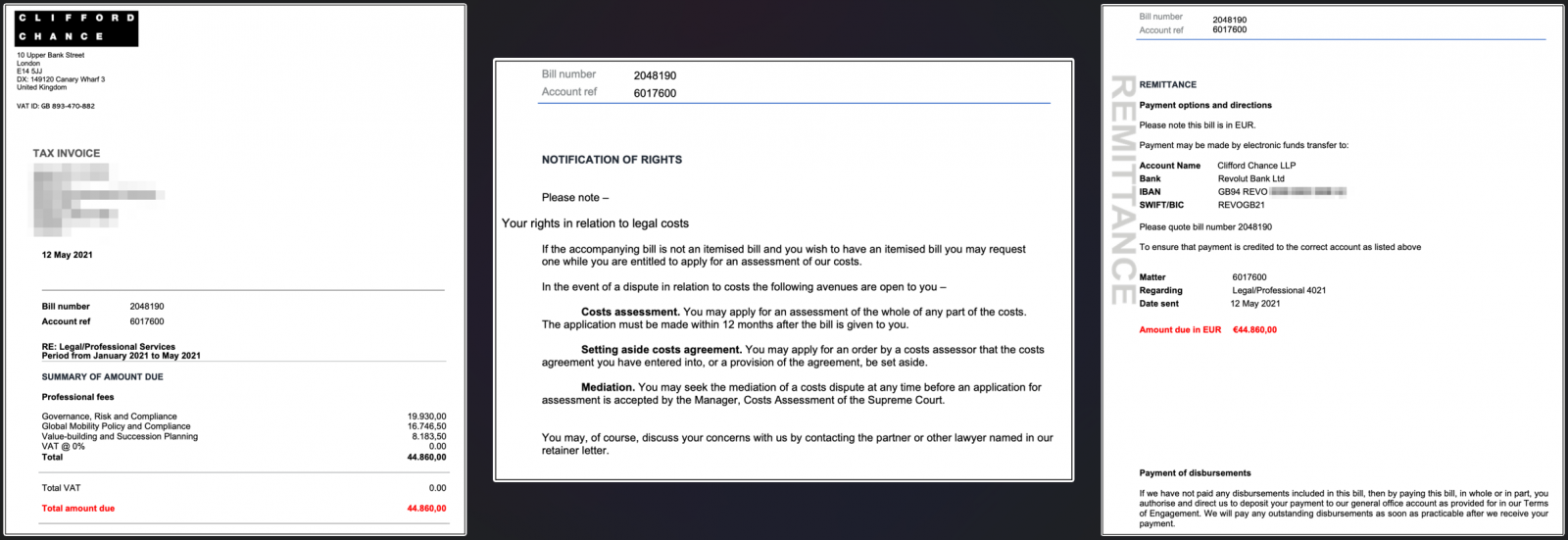
The law firms impersonated by Crimson Kingsnake include:
- Allen & Overy
- Clifford Chance
- Deloitte
- Dentons
- Eversheds Sutherland
- Herbert Smith Freehills
- Hogan Lovells
- Kirkland & Ellis
- Lindsay Hart
- Manix Law Firm
- Monlex International
- Morrison Foerster
- Simmons & Simmons
- Sullivan & Cromwell
These are major multinational firms with a global footprint, so the threat actors assume the target will recognize them, which adds legitimacy to the email.
Crimson Kingsnake attacks
The phishing emails don't target specific industries or countries but are distributed somewhat randomly in what Abnormal Security calls "blind BEC attacks."
If any recipients fall for the bait and request more information about the invoice, Crimson Kingsnake responds by providing a fake description of the provided service.
In some cases where the BEC actors meet resistance, they add a false "reply" from an executive in the targeted company to approve the transaction.
"When the group meets resistance from a targeted employee, Crimson Kingsnake occasionally adapts their tactics to impersonate a second persona: an executive at the targeted company," explains the report by Abnormal Security.
"When a Crimson Kingsnake actor is questioned about the purpose of an invoice payment, we've observed instances where the attacker sends a new email with a display name mimicking a company executive."
"In this email, the actor clarifies the purpose of the invoice, often referencing something that supposedly happened several months before, and “authorizes” the employee to proceed with the payment."
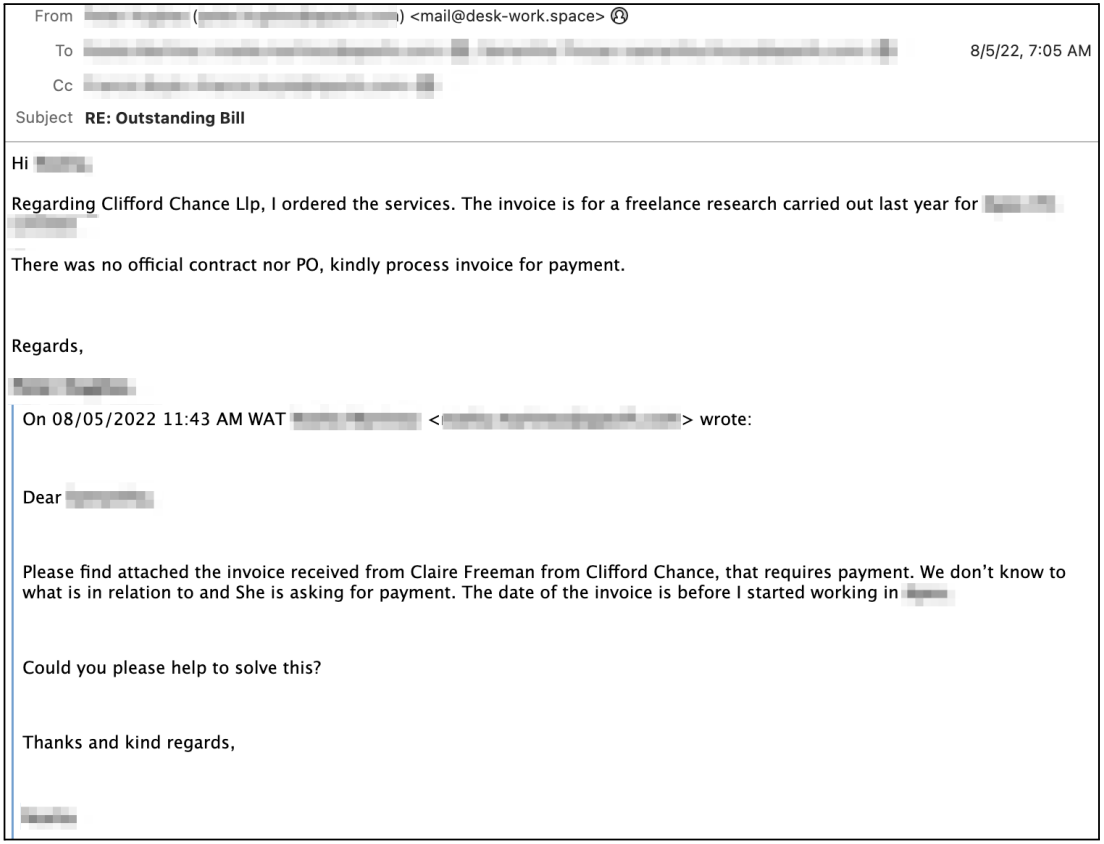
While the email originates from outside the company, the executive's email address can still trick the recipient, especially if there are no mailbox filters and warning systems to alert the targeted employee.
BEC attacks rising
BEC attacks are only a tiny part of all the daily phishing emails circulating in global inboxes, but even in these low volumes, it’s still a multi-billion problem.
According to the FBI, from 2016 until 2019, reported cases of BEC-induced losses amounted to $43 billion, while in 2021 alone, the IC3 recorded $2.4 billion lost by 19,954 entities to BEC scams.
Abnormal Security’s H1 2022 Email Threat Report also reports a rise in BEC attacks by 84% in H2 ‘21, measuring an average of 0.82 emails per 1,000 inboxes.
According to the same report, organizations with over 50,000 employees have a 95% chance of receiving a BEC email weekly.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now