
Almost twenty car manufacturers and services contained API security vulnerabilities that could have allowed hackers to perform malicious activity, ranging from unlocking, starting, and tracking cars to exposing customers' personal information.
The security flaws impacted well-known brands, including BMW, Roll Royce, Mercedes-Benz, Ferrari, Porsche, Jaguar, Land Rover, Ford, KIA, Honda, Infiniti, Nissan, Acura, Hyundai, Toyota, and Genesis.
The vulnerabilities also affected vehicle technology brands Spireon, Reviver, and SiriusXM Connected Vehicle Services.
The discovery of these API flaws comes from a team of researchers led by Sam Curry, who previously disclosed Hyundai, Genesis, Honda, Acura, Nissan, Infinity, and SiriusXM security issues in November 2022.
While Curry's previous disclosure explained how hackers could use these flaws to unlock and start cars, now that a 90-day vulnerability disclosure period has passed since reporting these issues, the team has published a more detailed blog post about the API vulnerabilities.
The impacted vendors have fixed all issues presented in this report, so they are not exploitable now.
Accessing internal portals
The most severe API flaws were found in BMW and Mercedes-Benz, which were affected by company-wide SSO (single-sign-on) vulnerabilities that enabled attackers to access internal systems.
For Mercedes-Benz, the analysts could access multiple private GitHub instances, internal chat channels on Mattermost, servers, Jenkins and AWS instances, XENTRY systems that connect to customer cars, and more.
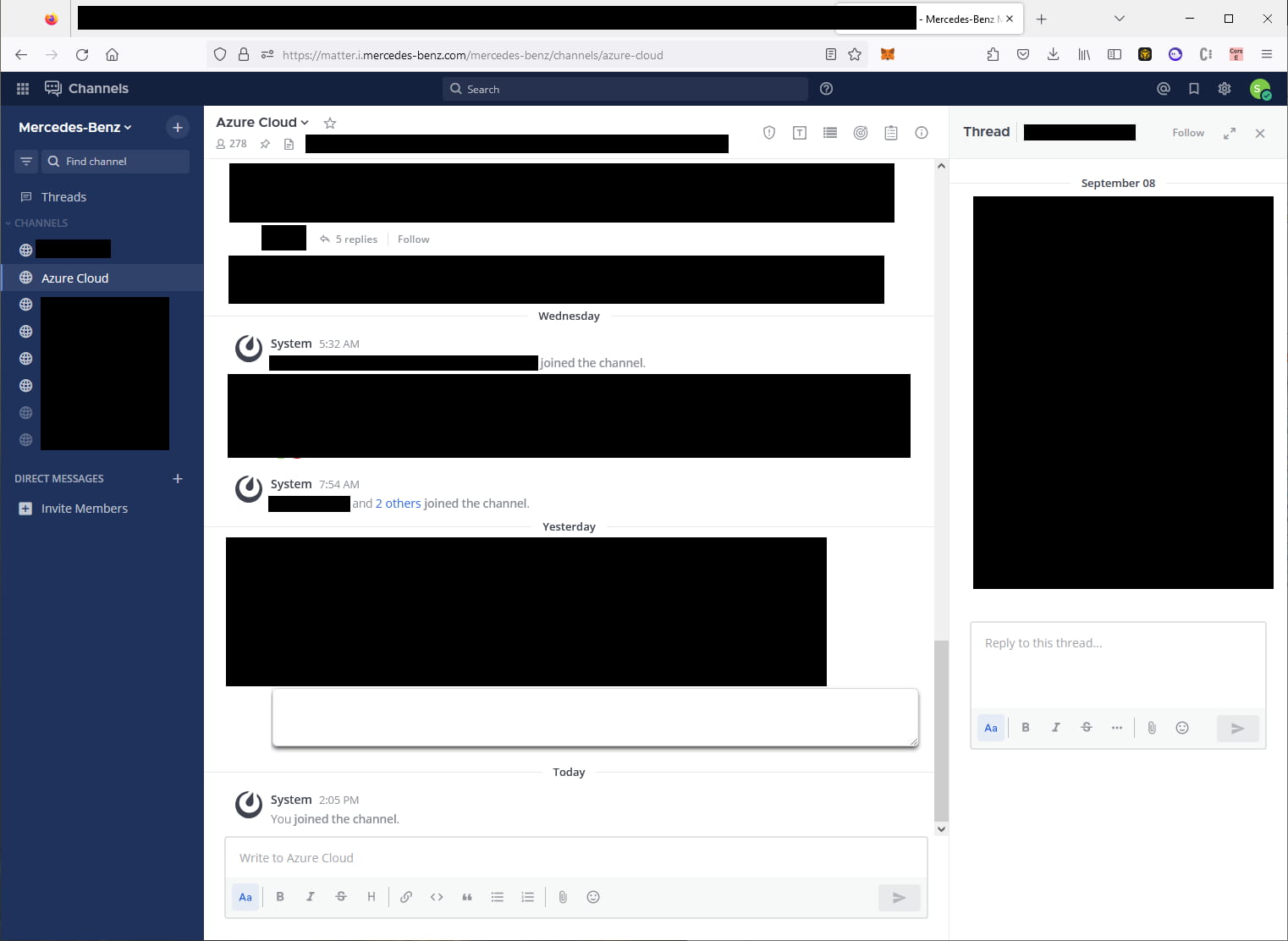
Source: Sam Curry
For BMW, the researchers could access internal dealer portals, query VINs for any car, and retrieve sales documents containing sensitive owner details.
Additionally, they could leverage the SSO flaws to log in as any employee or dealer and access applications reserved for internal use.
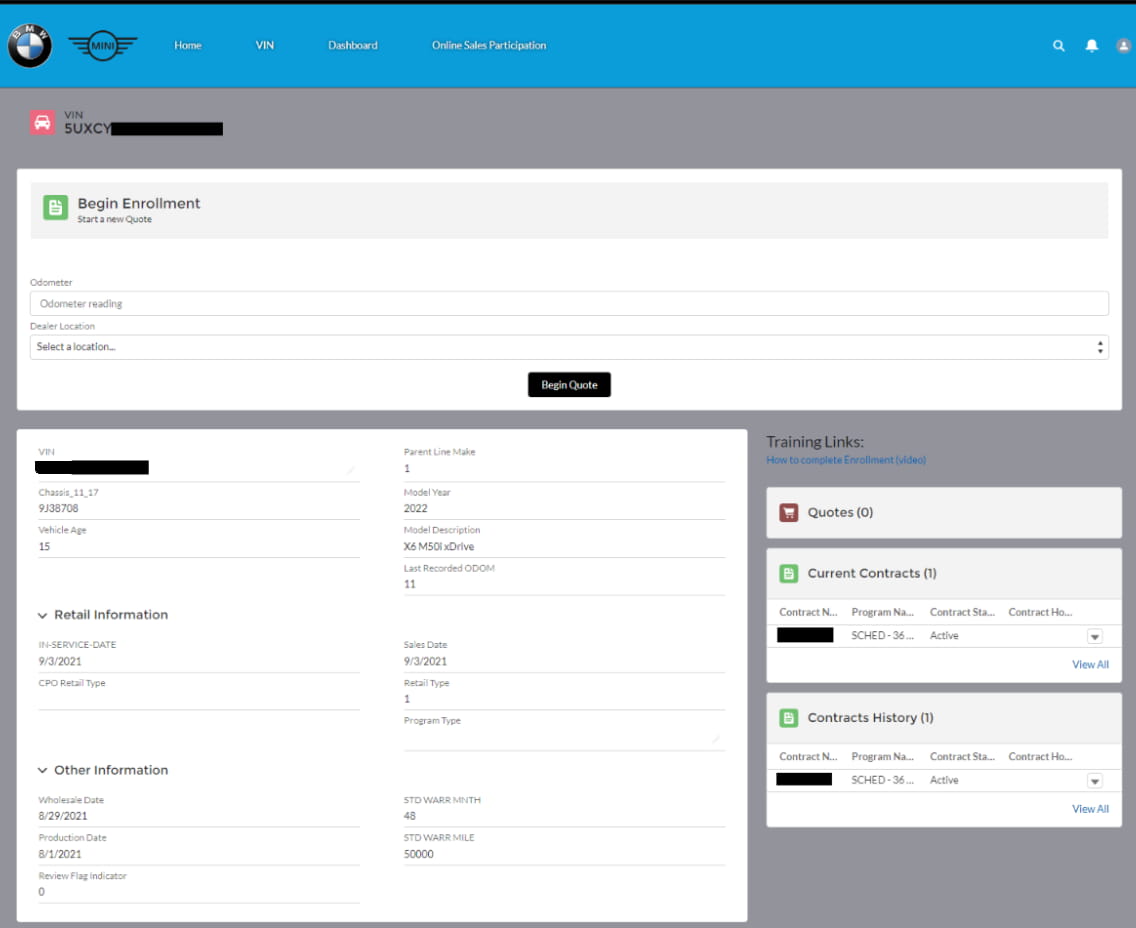
Source: Sam Curry
Exposing owner details
Exploiting other API flaws allowed the researchers to access PII (personally identifiable information) for owners of KIA, Honda, Infiniti, Nissan, Acura, Mercedes-Benz, Hyundai, Genesis, BMW, Roll Royce, Ferrari, Ford, Porsche, and Toyota cars.
In the cases of ultra-expensive cars, disclosing owner information is particularly dangerous as, in some cases, the data includes sales information, physical location, and customer addresses.
Ferrari suffered from poorly implemented SSO on its CMS, exposing backend API routes and making it possible to extract credentials from JavaScript snippets.
An attacker could exploit these flaws to access, modify, or delete any Ferrari customer account, manage their vehicle profile, or set themselves as car owners.
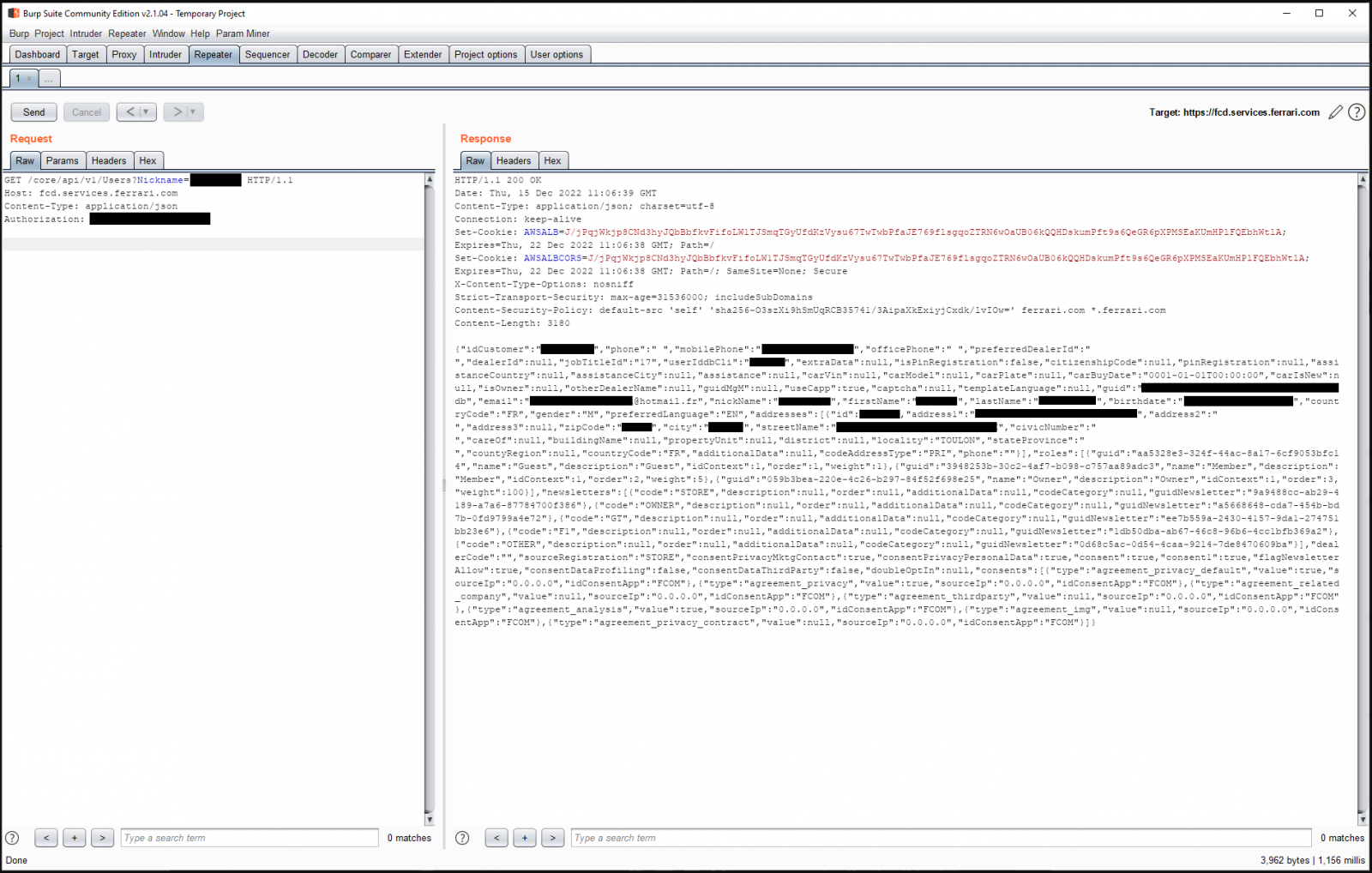
Source: Sam Curry
Tracking vehicle GPS
These vulnerabilities could have also allowed hackers to track cars in real time, introducing potential physical risks and impacting the privacy of millions of car owners.
Porsche was one of the impacted brands, with flaws in its telematic systems enabling attackers to retrieve vehicle locations and send commands.
GPS tracking solution Spireon was also vulnerable to car location disclosure, impacting 15.5 million vehicles using its services and even letting full administration access to its remote management panel, enabling attackers to unlock cars, start the engine, or disable the starter.
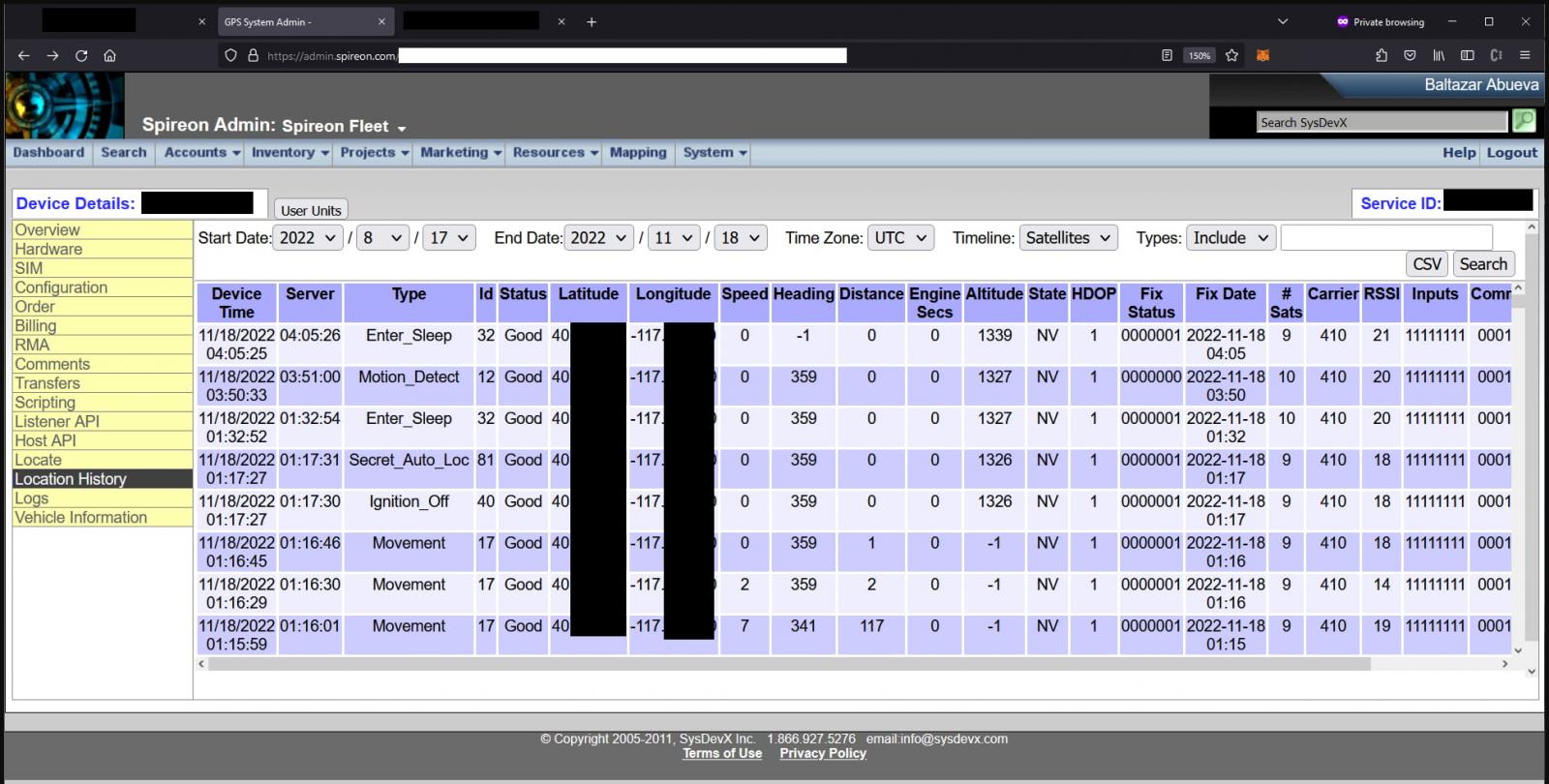
Source: Sam Curry
The third impacted entity is Reviver, a digital license plate maker that was vulnerable to unauthenticated, remote access to its admin panel that could have given anyone access to GPS data and user records, the ability to change license plate messaging, and more.
Curry illustrates how these flaws allowed them to mark a vehicle as "STOLEN" on the Reviver panel, which would automatically inform the police about the incident, putting the owner/driver at unnecessary risk.
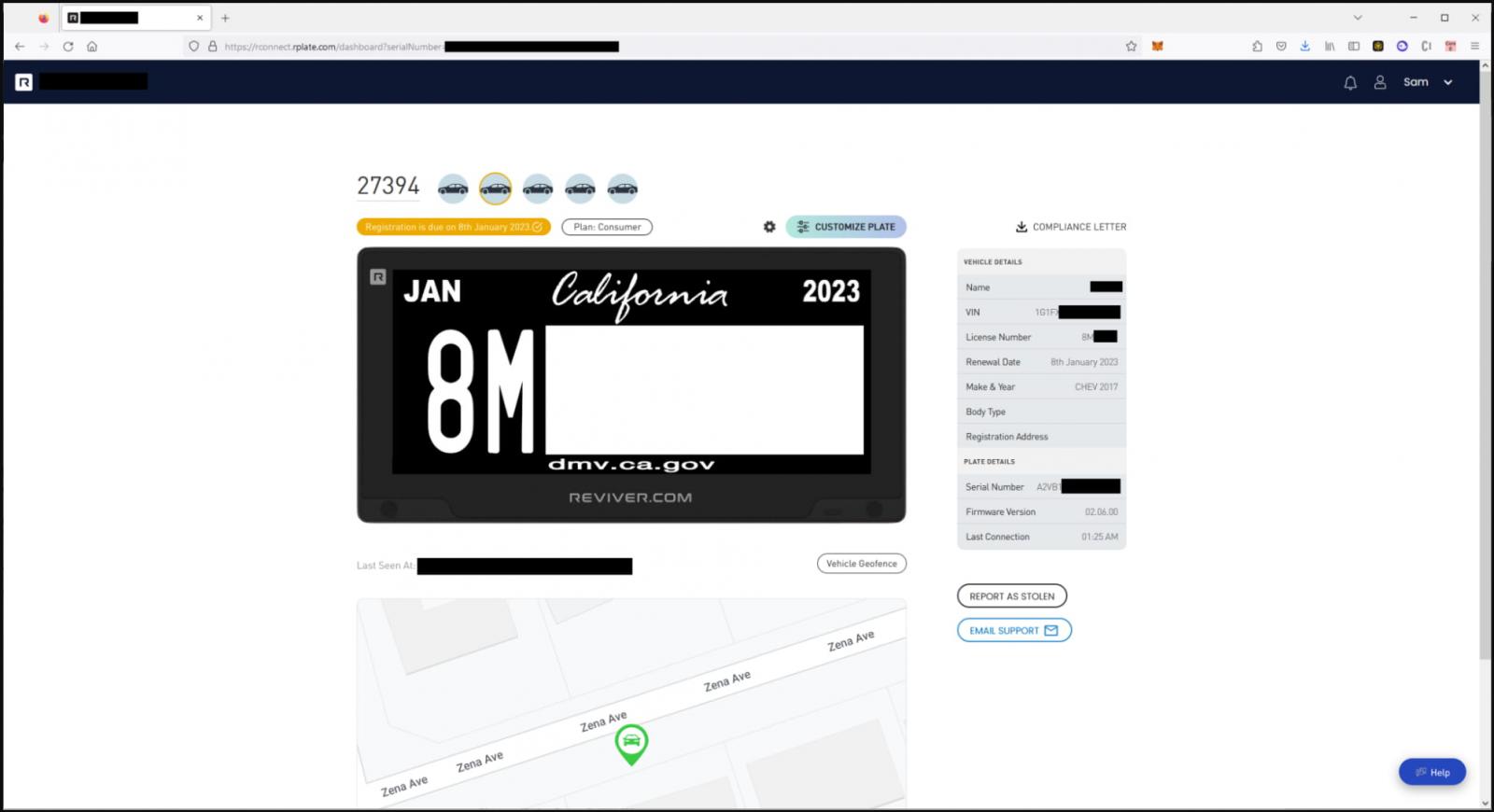
Source: Sam Curry
Minimizing exposure
Car owners can protect themselves from these types of vulnerabilities by limiting the amount of personal information stored in vehicles or mobile companion apps.
It is also essential to set in-car telematics to the most private mode available and read privacy policies to understand how data is being used.
Sam Curry also shared the following advice with BleepingComputer that owners should follow when purchasing a car.
"When purchasing a used car, make sure that the prior owner's account has been removed. Use strong passwords and set up 2FA (two-factor authentication) if possible for apps and services which link to your vehicle," warned Curry in a statement to BleepingComputer.
Update 1/4 - A Spireon spokesperson has sent BleepingComputer the following comment:
Our cybersecurity professionals met with the security researcher to discuss and evaluate the purported system vulnerabilities and immediately implemented remedial measures to the extent required.
We also took proactive steps to further strengthen the security across our product portfolio as part of our continuing commitment to our customers as a leading provider of aftermarket telematics solutions.
Spireon takes all security matters seriously and utilizes an extensive industry leading toolset to monitor and scan its products and services for both known and novel potential security risks.
Update 1/11 - A Reviver spokesperson has sent BleepingComputer the following comment:
We were recently contacted by a cybersecurity researcher regarding potential application vulnerabilities in the auto industry. Our team immediately investigated this report, met with the researcher, and, out of an abundance of caution, engaged leading data security and privacy professionals to assist.
We are proud of our team’s quick response, which patched our application in under 24 hours and took further measures to prevent this from occurring in the future.
Our investigation confirmed that this potential vulnerability has not been misused. Customer information has not been affected, and there is no evidence of ongoing risk related to this report.
As part of our commitment to data security and privacy, we also used this opportunity to identify and implement additional safeguards to supplement our existing, significant protections.
Cybersecurity is central to our mission to modernize the driving experience and we will continue to work with industry-leading professionals, tools, and systems to build and monitor our secure platforms for connected vehicles.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now